In the previous three post we went through installing and configuring the vROPs virtual appliance, connecting to vCenter server and configuring Window Active directory as an identity source.
Part 1: Install and Configure vRealize Operations Manager 8.2 Part 1 – TheSleepyAdmins
Part 2: Install and Configure vRealize Operations Manager 8.2 Part 2 Connect to vCenter – TheSleepyAdmins
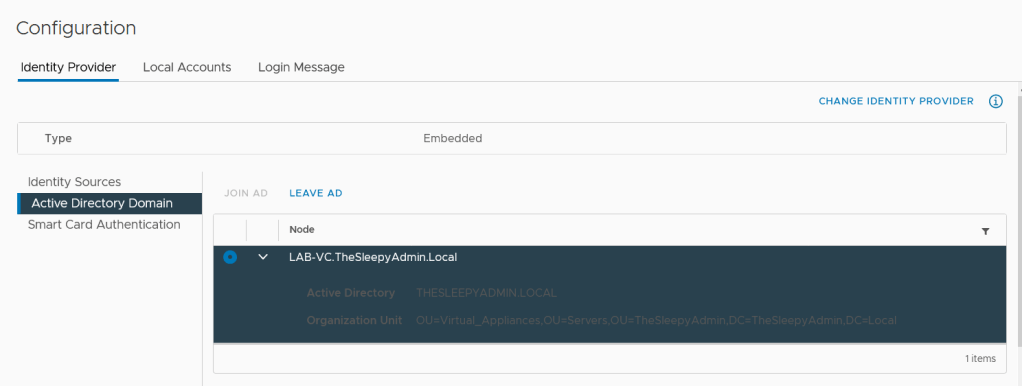
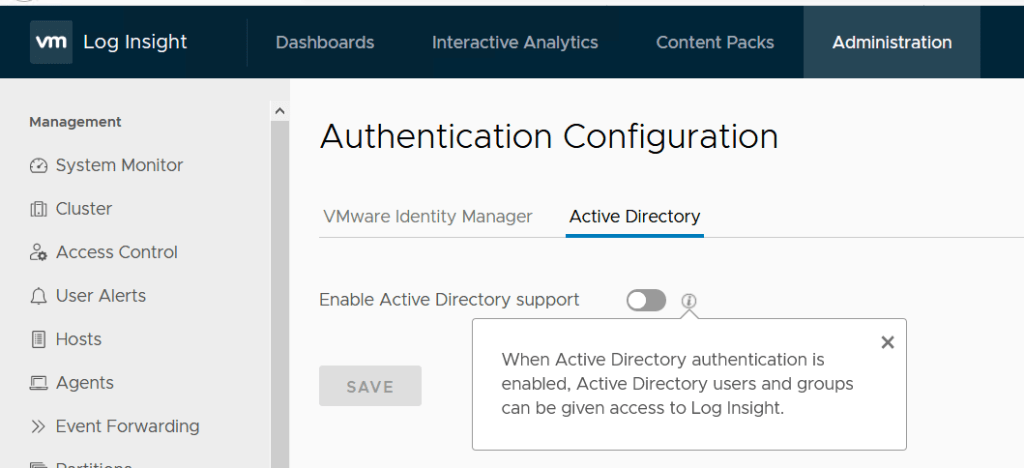
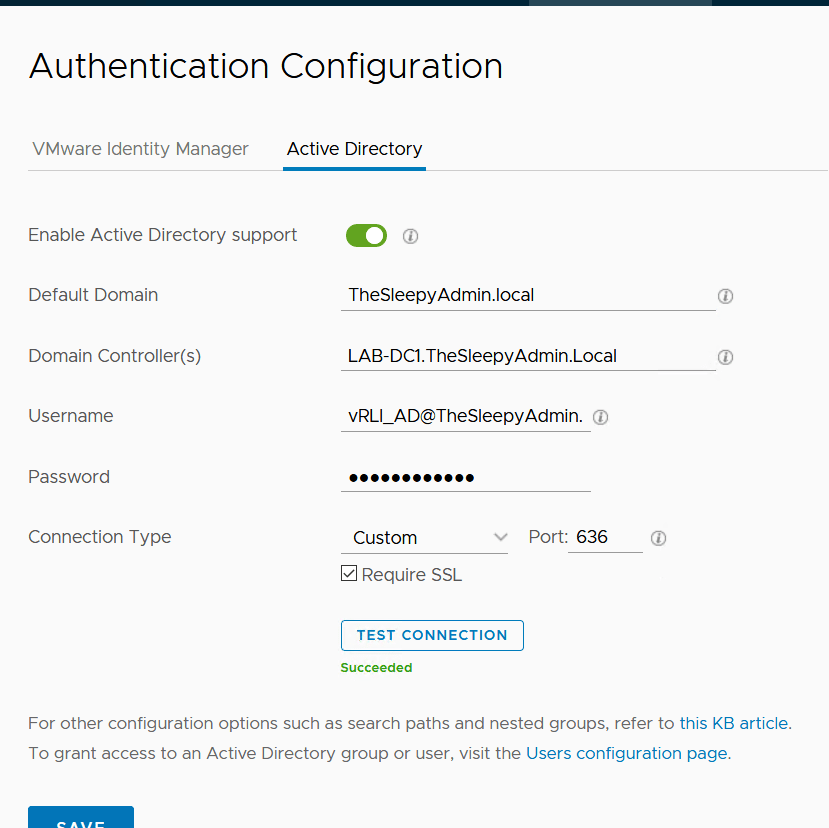
Part 3: Install and Configure vRealize Operations Manager 8.2 Part 3 AD Authentication – TheSleepyAdmins
In this post we will be going through the different alert types and configuring actions bases on certain alerts.
Alerts:
Below are the three types of alert in vROPs:
Health Alerts:
The health alert list is all the generated alerts that are configured to affect the health of your
environment and require immediate attention. You use the health alert list to evaluate,
prioritize, and immediately begin resolving the problems.
Risk Alerts:
The risk alerts list is all the generated alerts that are configured to indicate risk in your
environment. Address risk alerts in the near future, before the triggering symptoms that
generated the alert negatively affect the health of your environment.
Efficiency Alerts:
The efficiency alerts list is all the generated alerts that are configured to indicate problems
with the efficient use of your monitored objects in your environment. Address efficiency
alerts to reclaim wasted space or to improve the performance of objects in your environment.
Each alert type has four different severity types, info, warning, immediate and critical. The can all be configured
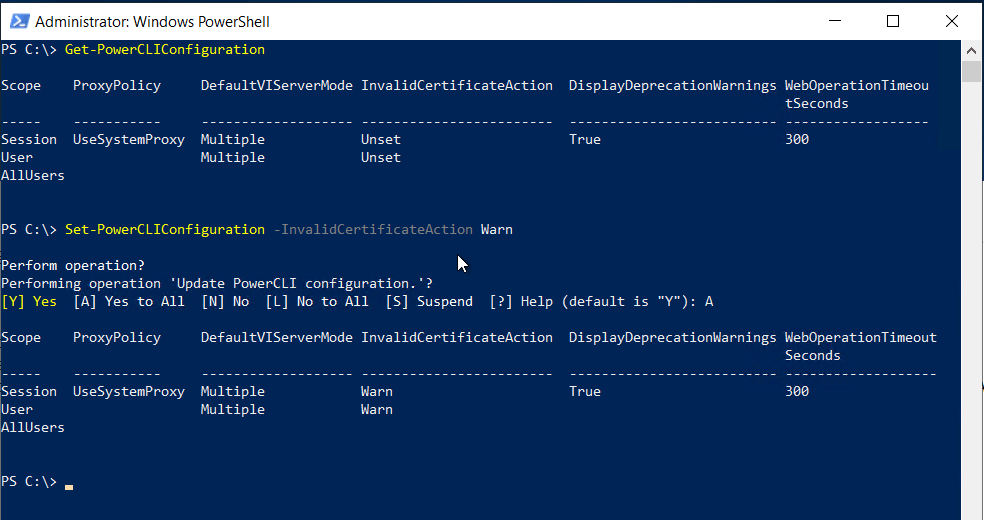
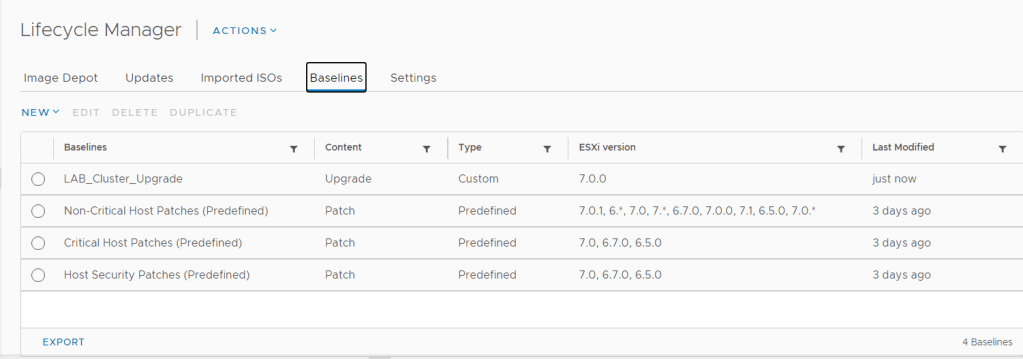
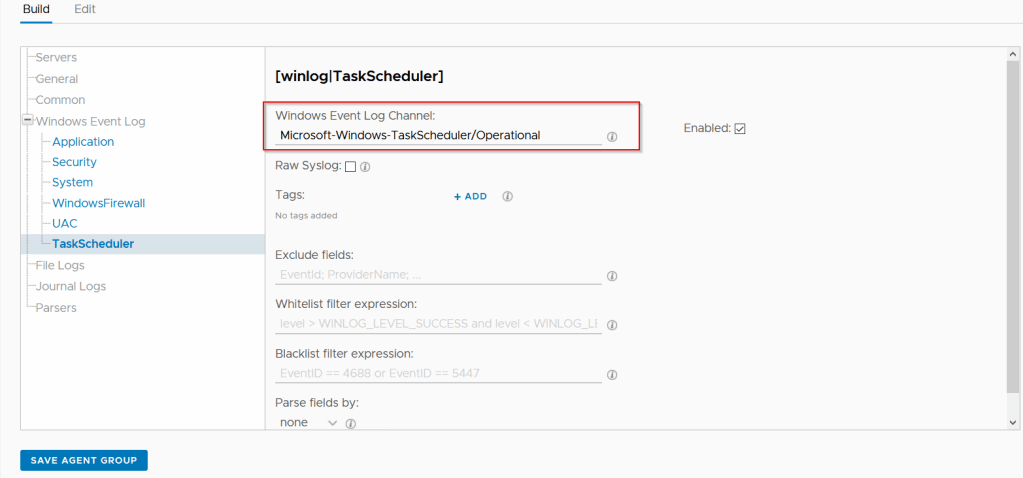
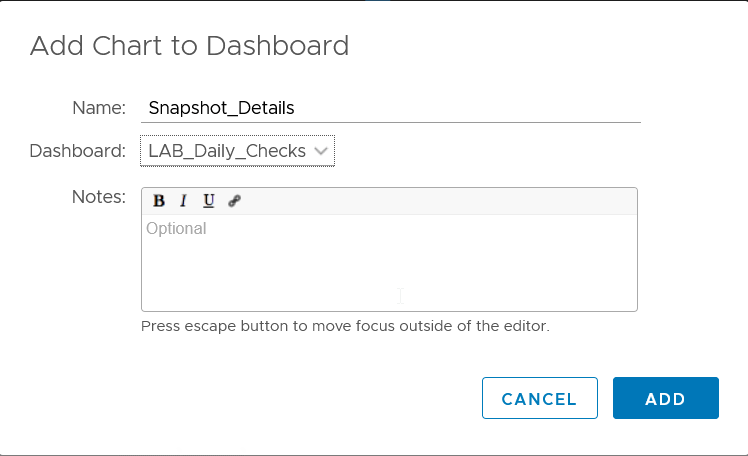
To create a custom alert logon to vROPs web client > alerts > Alert Definitions
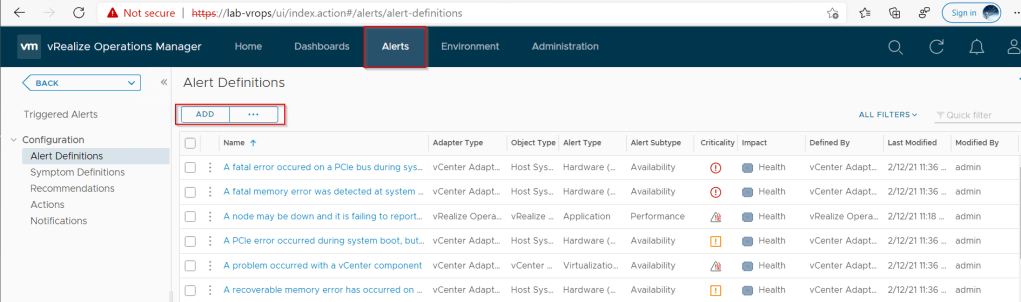
Click Add, give the alert a name
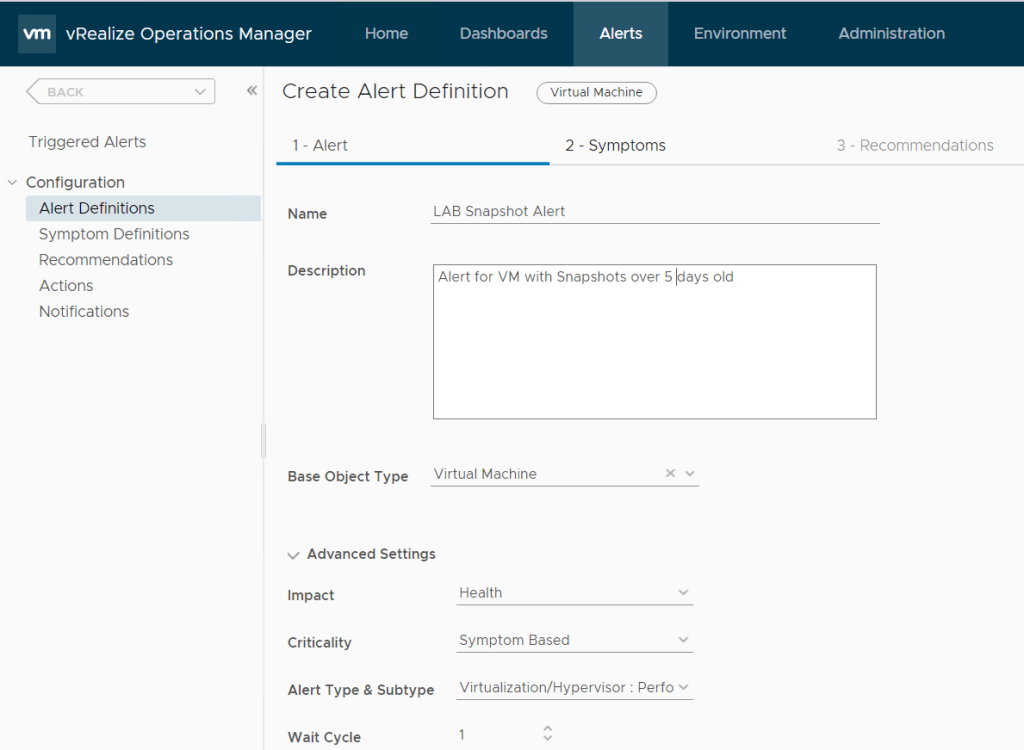
We will be using virtual machine so we will
select base object type and select vCenter Adapter > virtual Machine
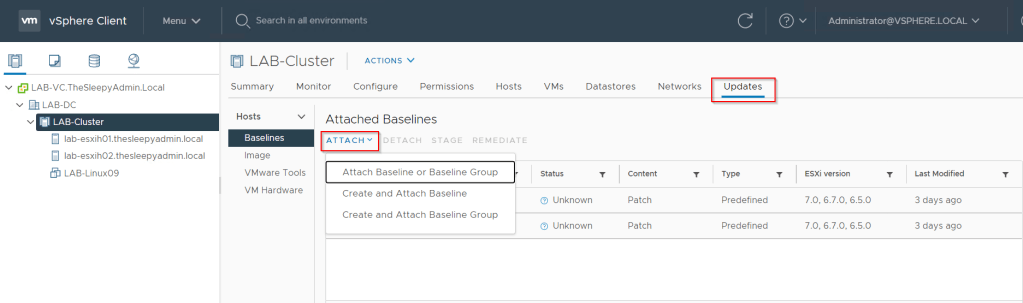
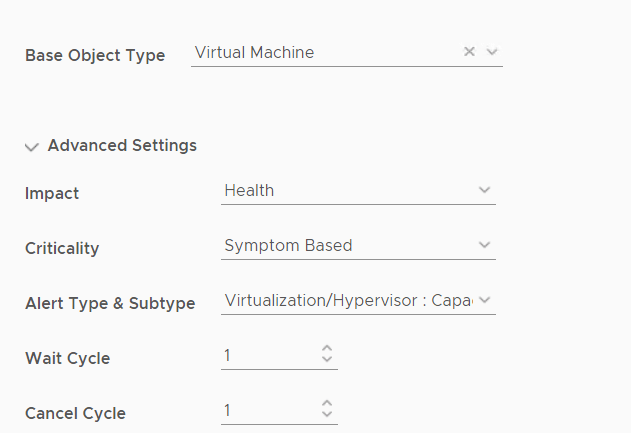
We want to alert on Capacity so click on advanced.
Impact = Health
Criticality = Symptom based
Alert Type & Subtype = Virtualization/Hypervisor : Capacity
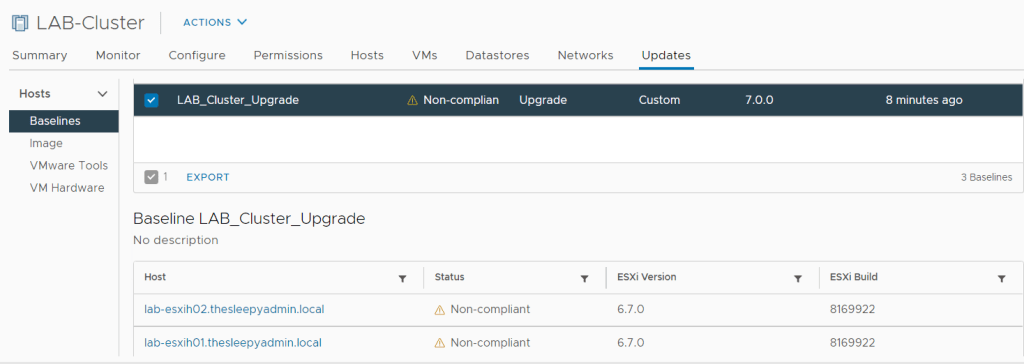
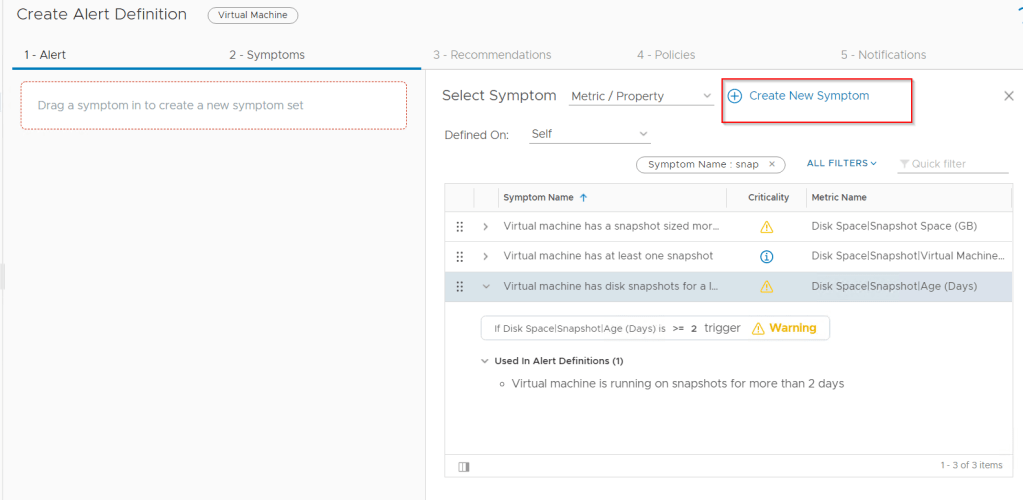
Next we need to add the a symptom that will be used to trigger the alert. If there is no symptom that matches what we want to alert on we can create a new symptom. For snapshot there is only greater than 2 days so we will create a new symptom.
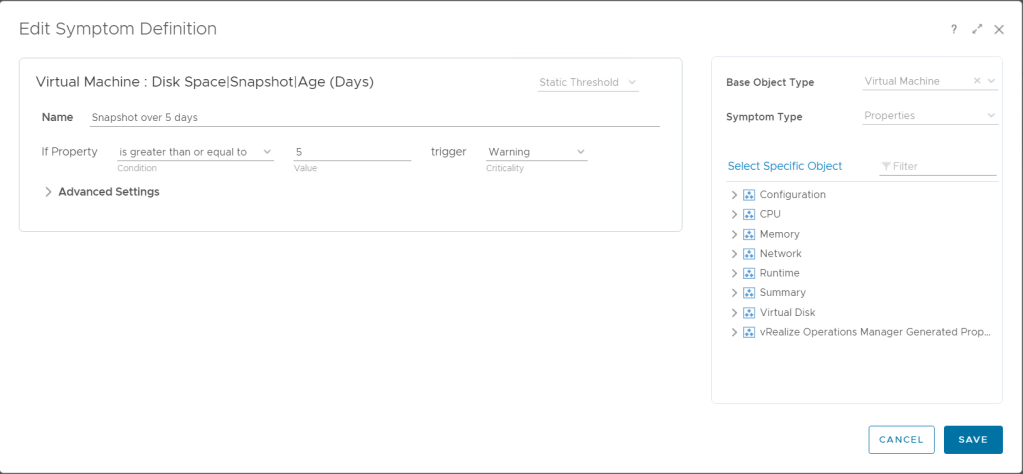
We will be using Virtual Machine: Disk space > Snapshot > Age (Days) and set the value to greater than 5 days.
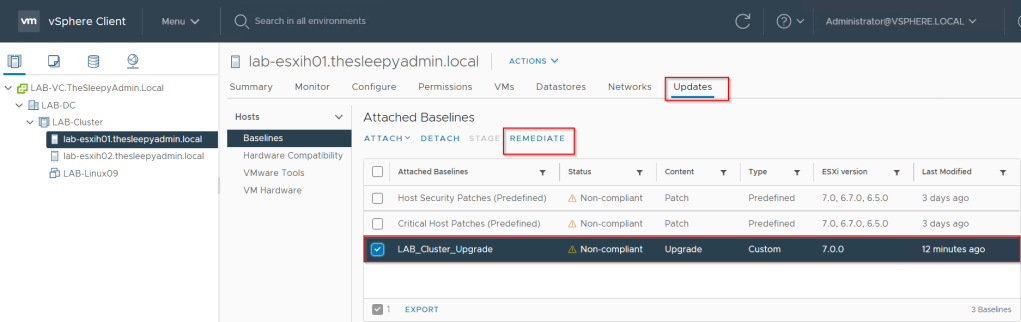
We can set a recommendation that already exists to not keep snapshots over 72 hours or create a custom recommendation.
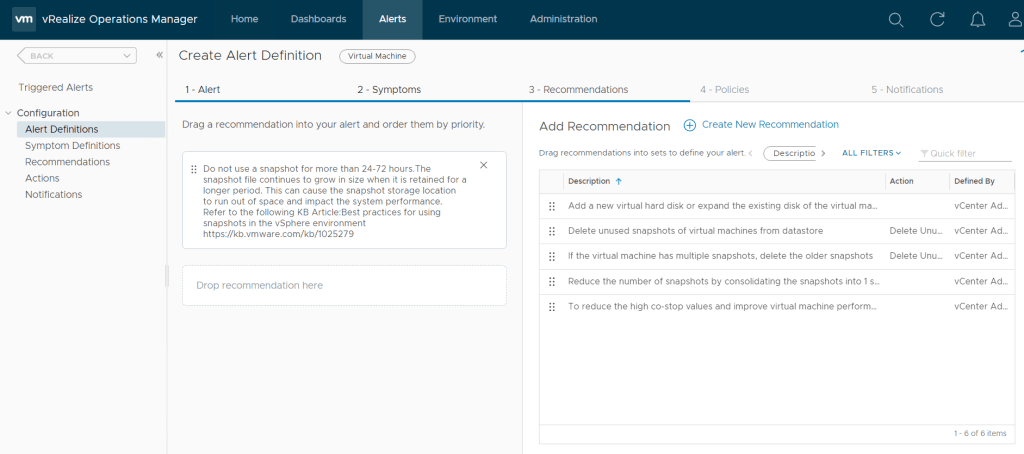
We can also apply a policy we will use the default policy.
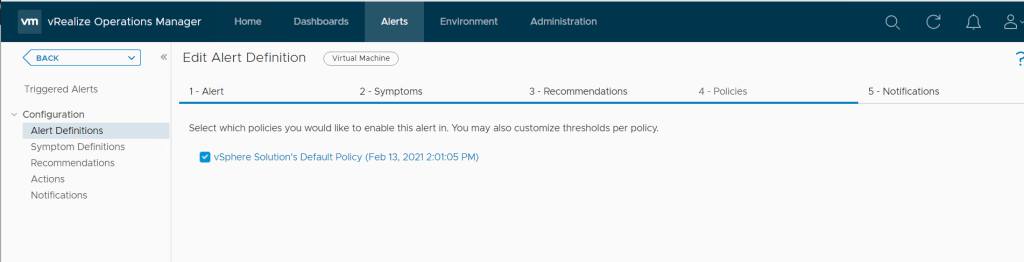
Complete the wizard to create the new alert.
Next we will configure an email notification instance to allow alerts to be emailed.
Go to Administration > Outbound Settings > Add
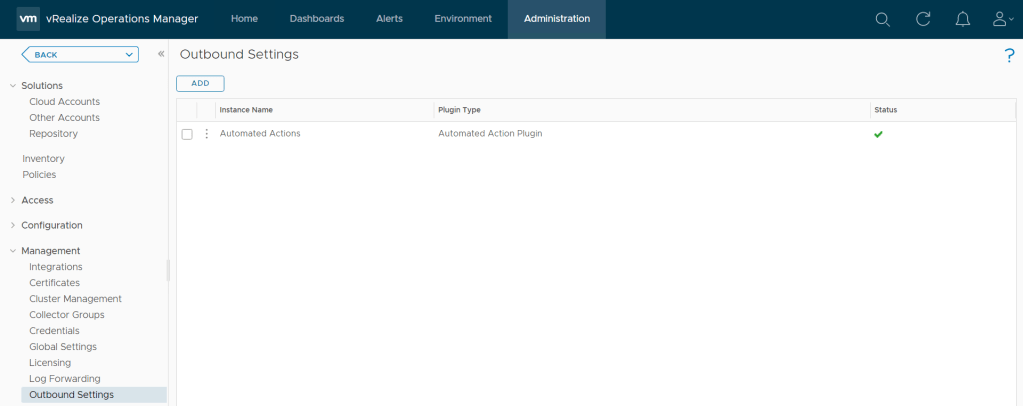
Added in the email servers settings.
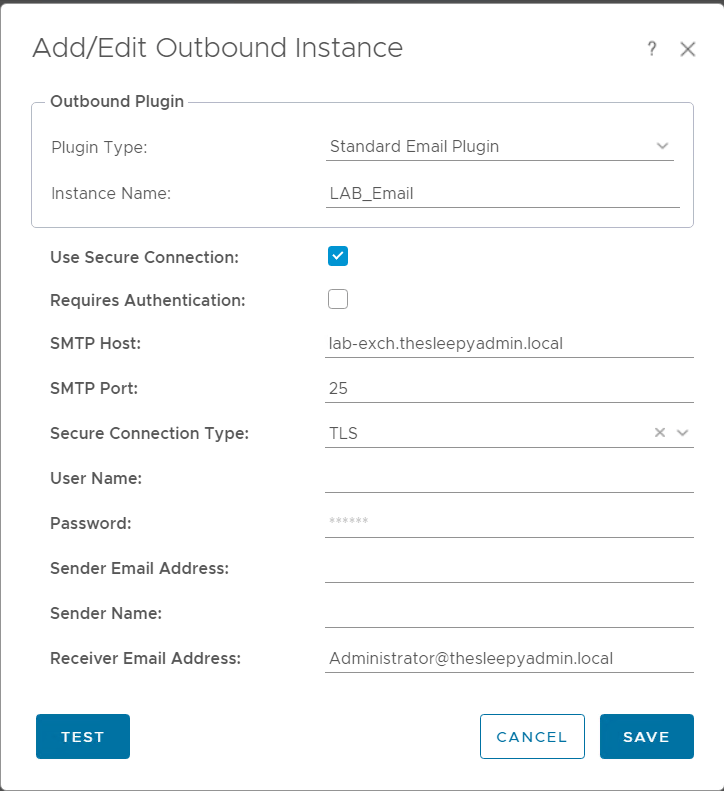
Click test to validate the mail flow is working.
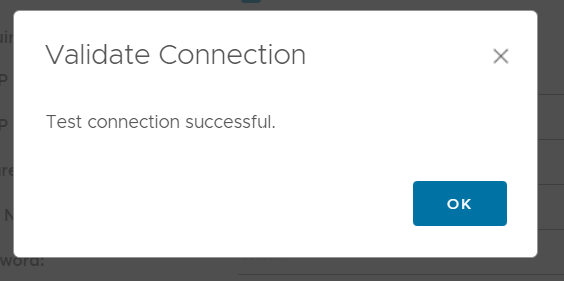
Click save to to complete.
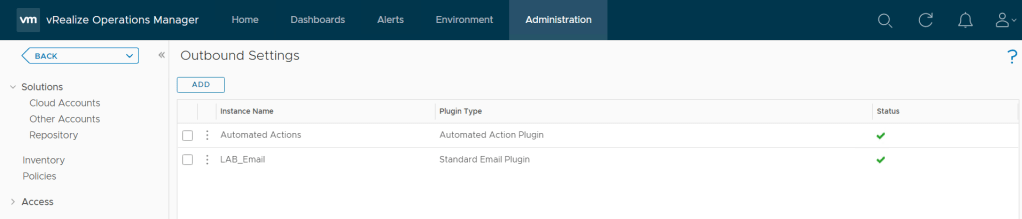
Once we have the outbound email instance configured, we can setup alerts to send emails notifications.
I created a new alert for Powered off VM so it would be easier to get a alert to trigger to test the email notification.
Go to Alerts > Notification
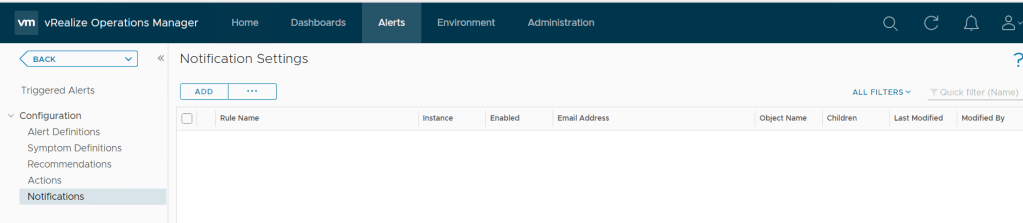
Next add in the details and select the email instance we setup earlier. I will be alerting for when LAB-Linux01 is powered off so will use object and specify the VM name and alert definition.
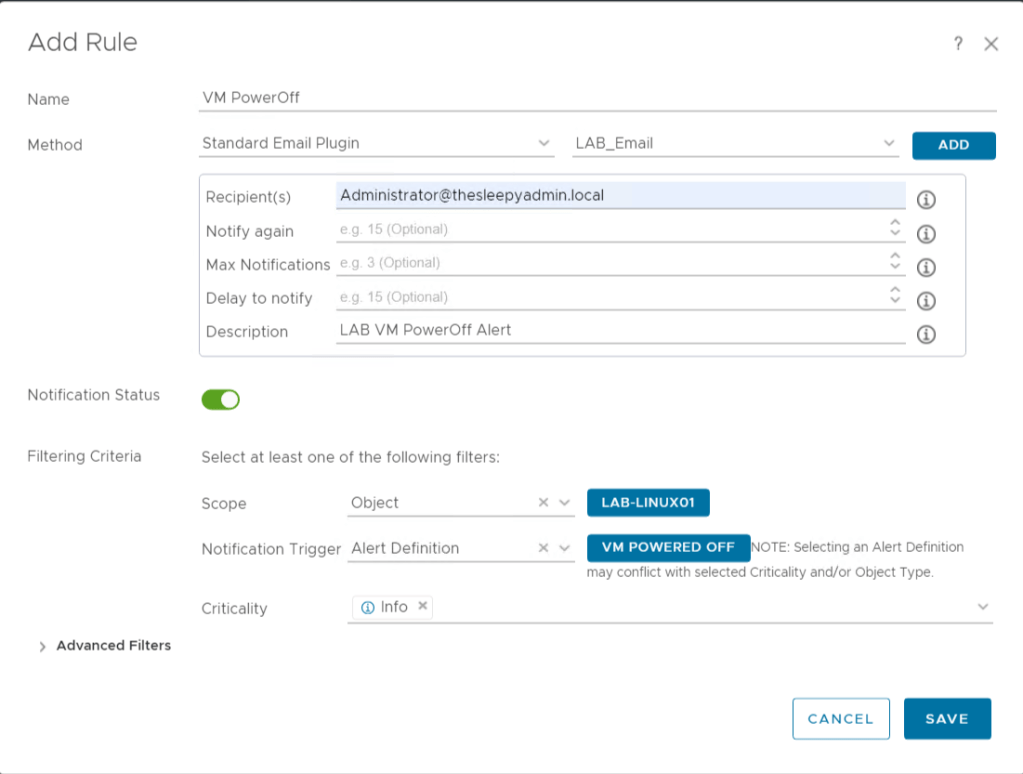
Click save to create the notification.
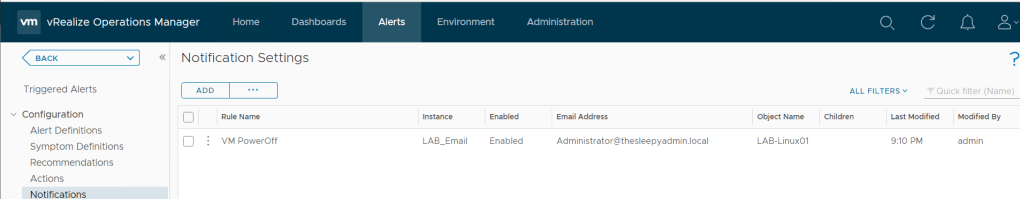
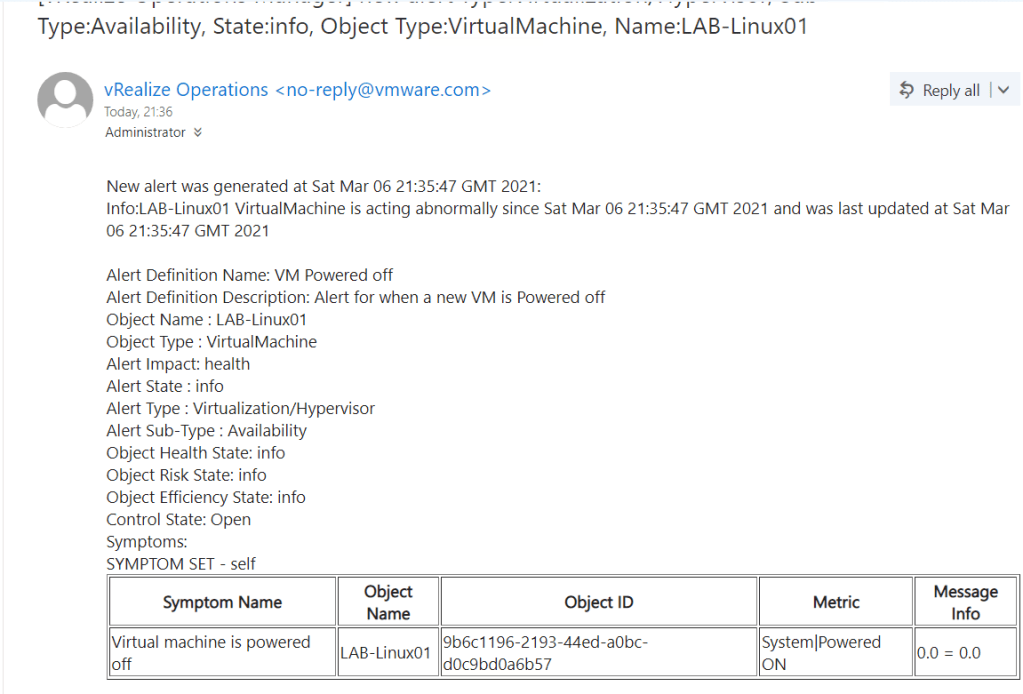
Now once the VM is powered off we will get an notification.
In the next post we will be going through creating a dashboard.