I have been looking at setting up MECM cloud management gateway (CMG) for a while but haven’t been able to, due to the need for PKI or Azure AD joined.
With the recent release of MECM 2002 this has added a new feature, that allows token based authentication. I decided to do a test deployment in my lab to see how this would work before deploying to our production environment.
With a CMG we can manage clients that don’t regularly connect back to the cooperate network which has become more of a priority recently.
There is a cost for running the VM’s in Azure that will be used as the CMG and for outbound data transfers. Johan Arwidmark has done a good real world cost estimates for a CMG.
First step should be to have a read of the docs for planning a CMG
https://docs.microsoft.com/en-us/mem/configmgr/core/clients/manage/cmg/plan-cloud-management-gateway
To use token base authentication require MECM 2002, so that is a pre-requisites for deploying a CMG in this way.
https://docs.microsoft.com/en-us/mem/configmgr/core/clients/deploy/deploy-clients-cmg-token
There will be some required permission in Azure also for deploying the CMG.
- Account that has Global Admin and Subscription Owner roles.
- Content filter rules to allow outbound access (If there is a proxy or Firewall filtering traffic)
There will also be a requirement for a cert to be applied to the CMG, it is recommend to have a third party cert as it should automatically trusted by clients.
From looking through the documents below are the required URL https://docs.microsoft.com/en-us/mem/configmgr/core/plan-design/network/internet-endpoints#cmg-connection-point
*.cloudapp.net
*.blob.core.windows.net
login.microsoftonline.com
Once all pre-requisites have been confirmed we can start to configure the CMG. We will need to pick a unique cloud service name as this will be required later, easiest way to check if the name you have select is unique is to logon to Azure go to cloud services (classic)
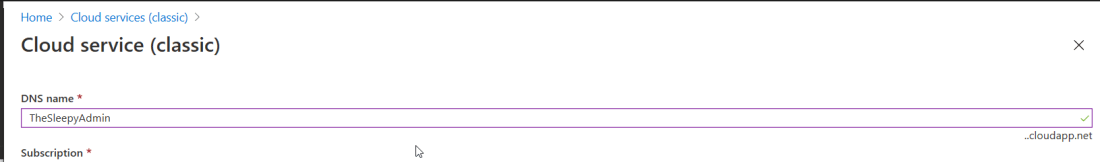
Once the cloud service has been checked, then we need to configure the Azure services.
Logon to the MECM console and go to Administration > Cloud services > Azure services.
Click configure Azure services
Give the service a name and select cloud management 
We need to configure a server and client applications 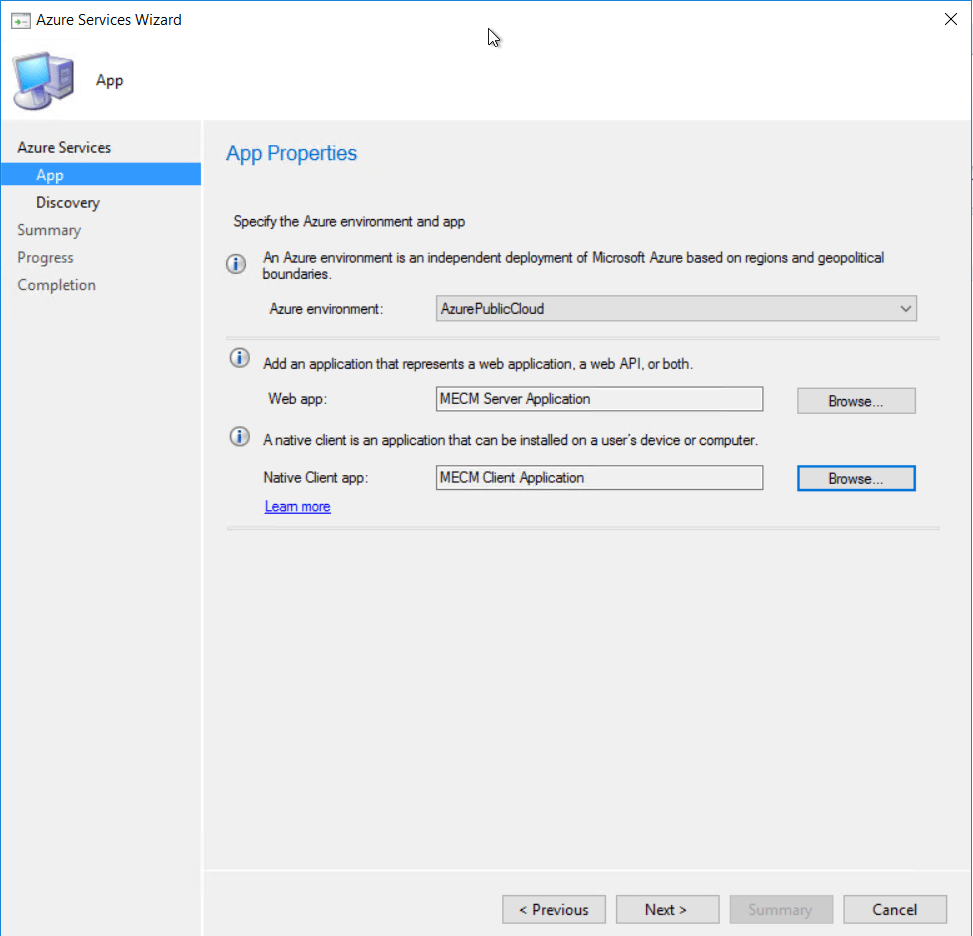 Give the applications a name and sign in to Azure using a account with the required permission
Give the applications a name and sign in to Azure using a account with the required permission 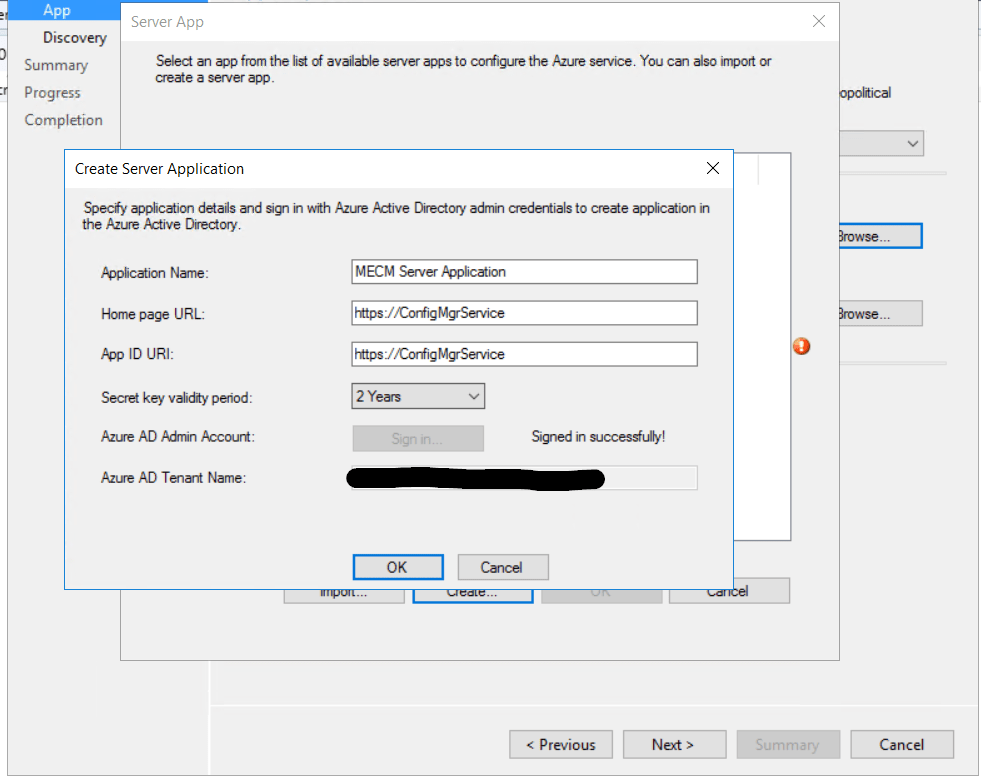
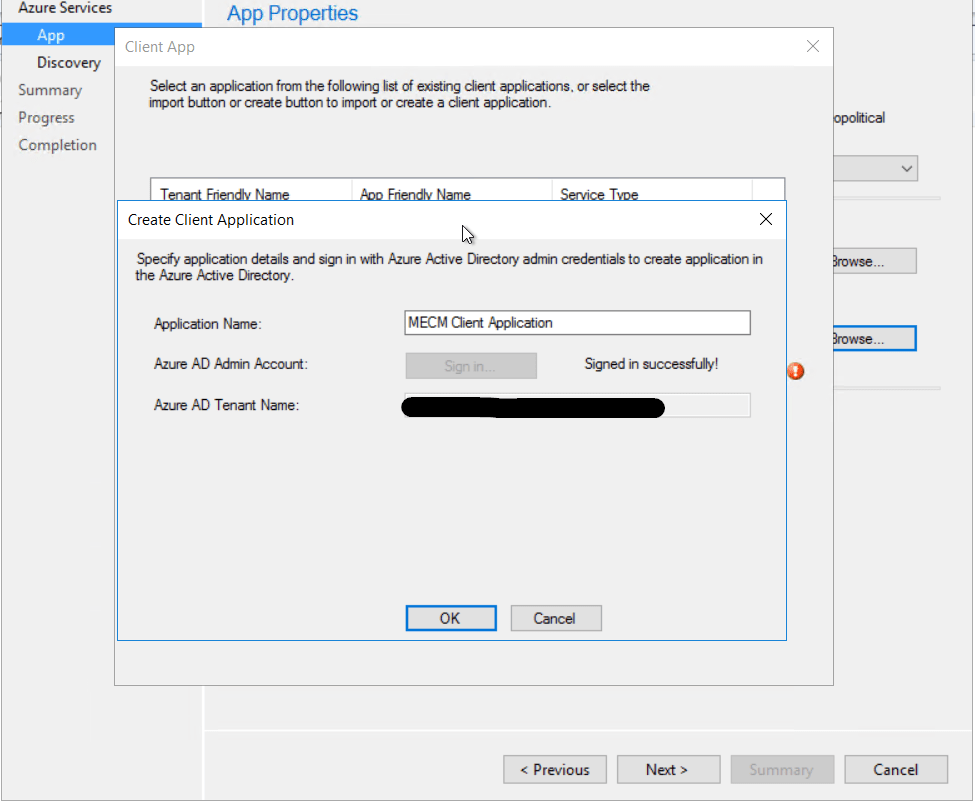 I just left user discovery enabled.
I just left user discovery enabled. 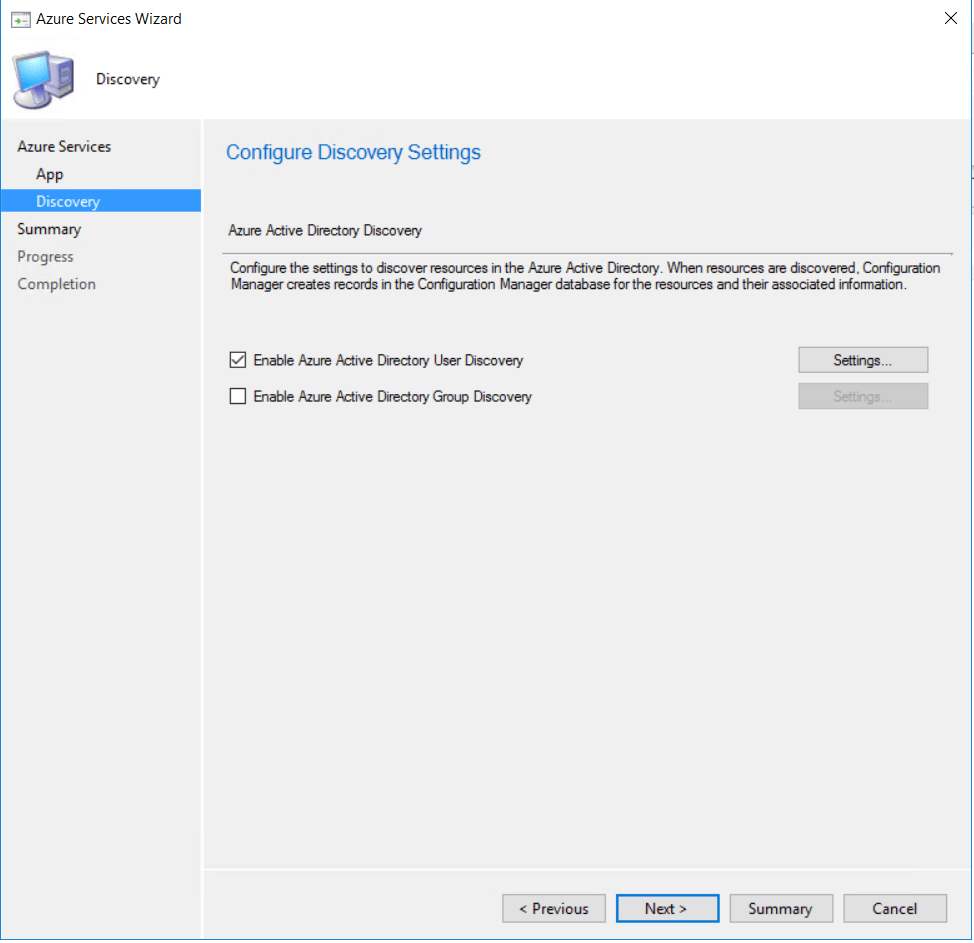 Click next to finish configuring the Azure services.
Click next to finish configuring the Azure services.  Once finished the Azure service should now be showing
Once finished the Azure service should now be showing 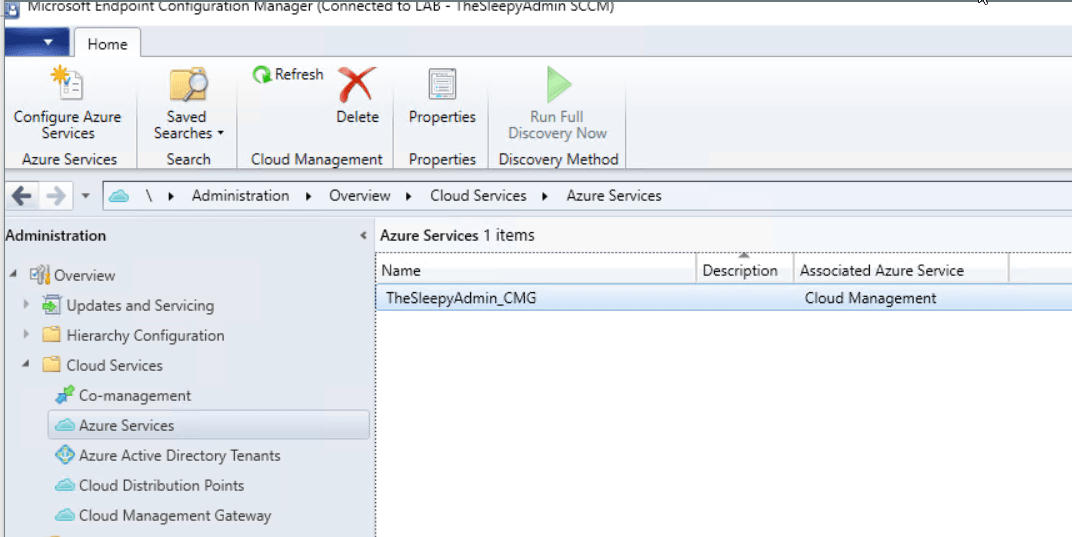 The Azure AD tenant should also show with both application we just created.
The Azure AD tenant should also show with both application we just created. 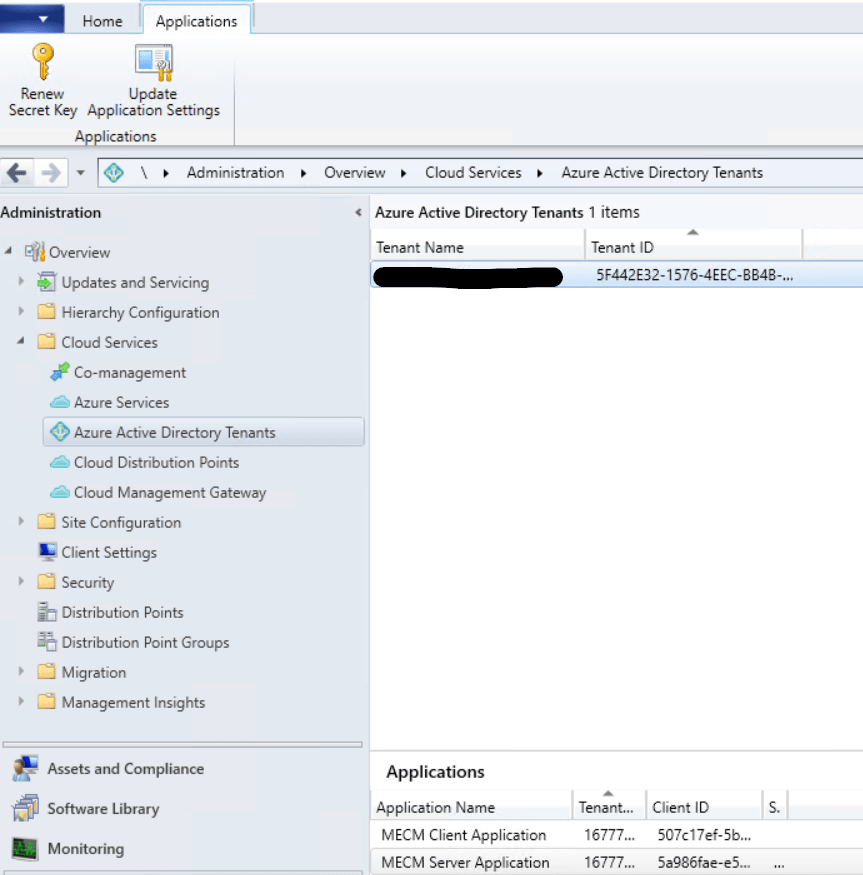
Once this has all been configured we can now start to setup the CMG.
To start the configuration go to Administration > Cloud services > Cloud Management Gateway
Click Create Cloud Management Gateway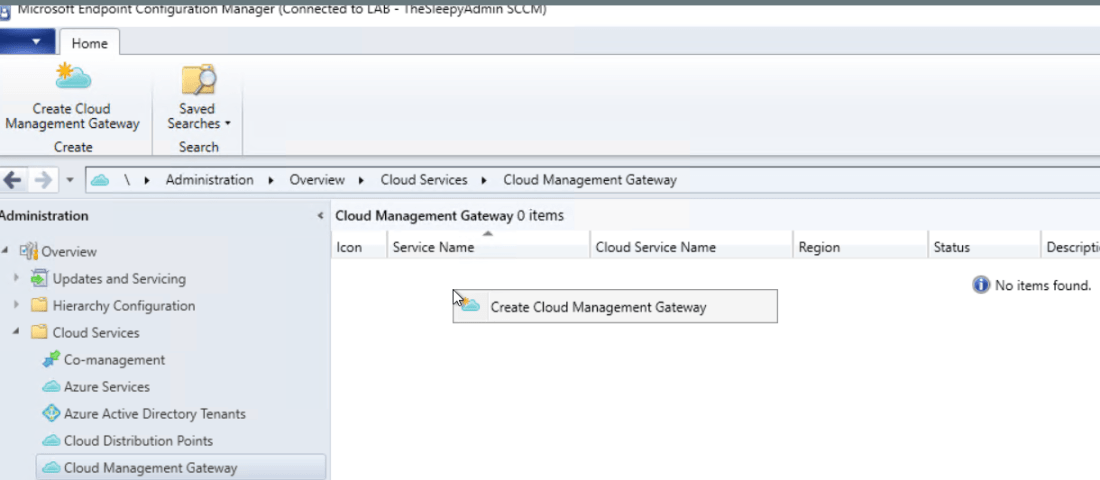
Select AzurePublicCloud and sign in. (If the subscription ID doesn’t show it might be the account you are using is not an owner of the subscription.)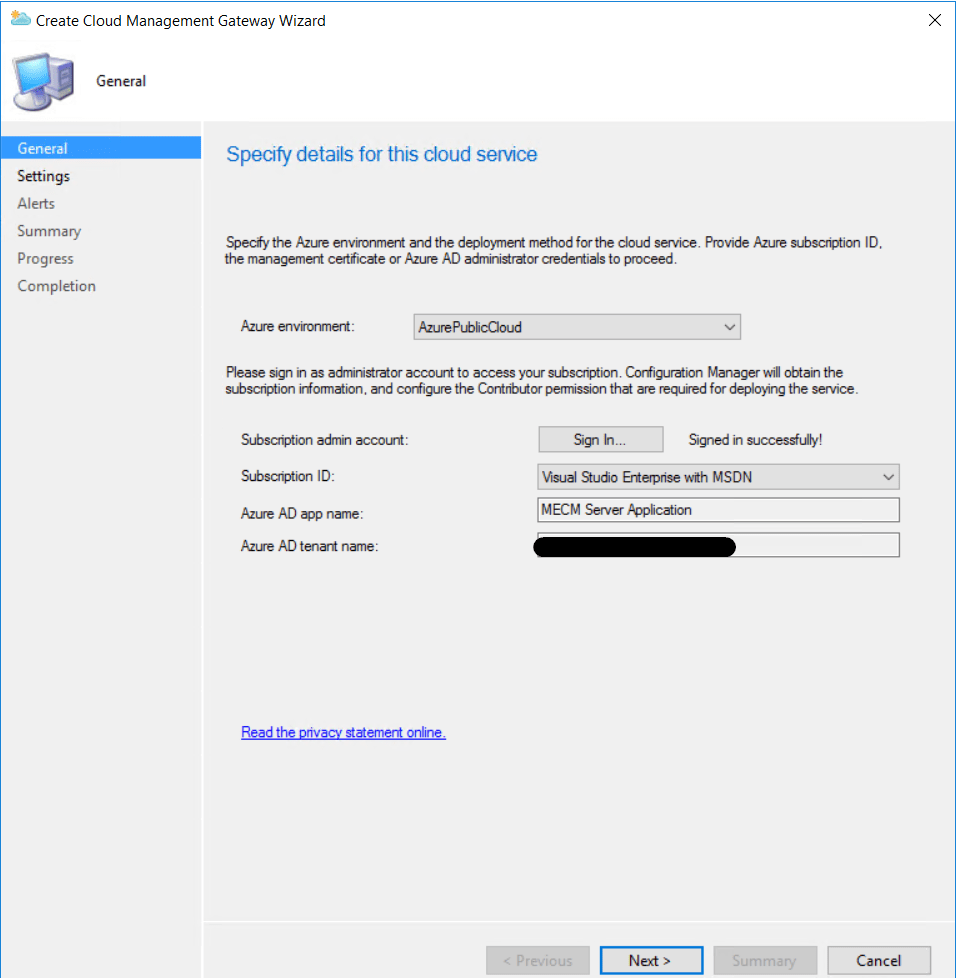
Now we need to configure the cloud services, this is where we will use the name we checked earlier.
- Select the cert file, this needs to be a PFX with the private key (I am using one created on my internal CA but in production I will be using a third party CA like digicert or godaddy)
- The cert name will be automatically set the deployment services name so this is why we should confirm the name before hand so we can generate the cert with the same name.
- Select the region the CMG will be configured in
- Either select a existing or create a new resource group (I chose new one to keep the CMG separate from my other Azure resources)
- Select the required amount of VM’s this can go up to 16 (for high availability it recommend to configure 2 VM’s at least)
- Tick the required security authentication I just ticked Enforce TLS 1.2
- I also ticked using CMG and cloud distribution point
 I left the alerting as default
I left the alerting as default 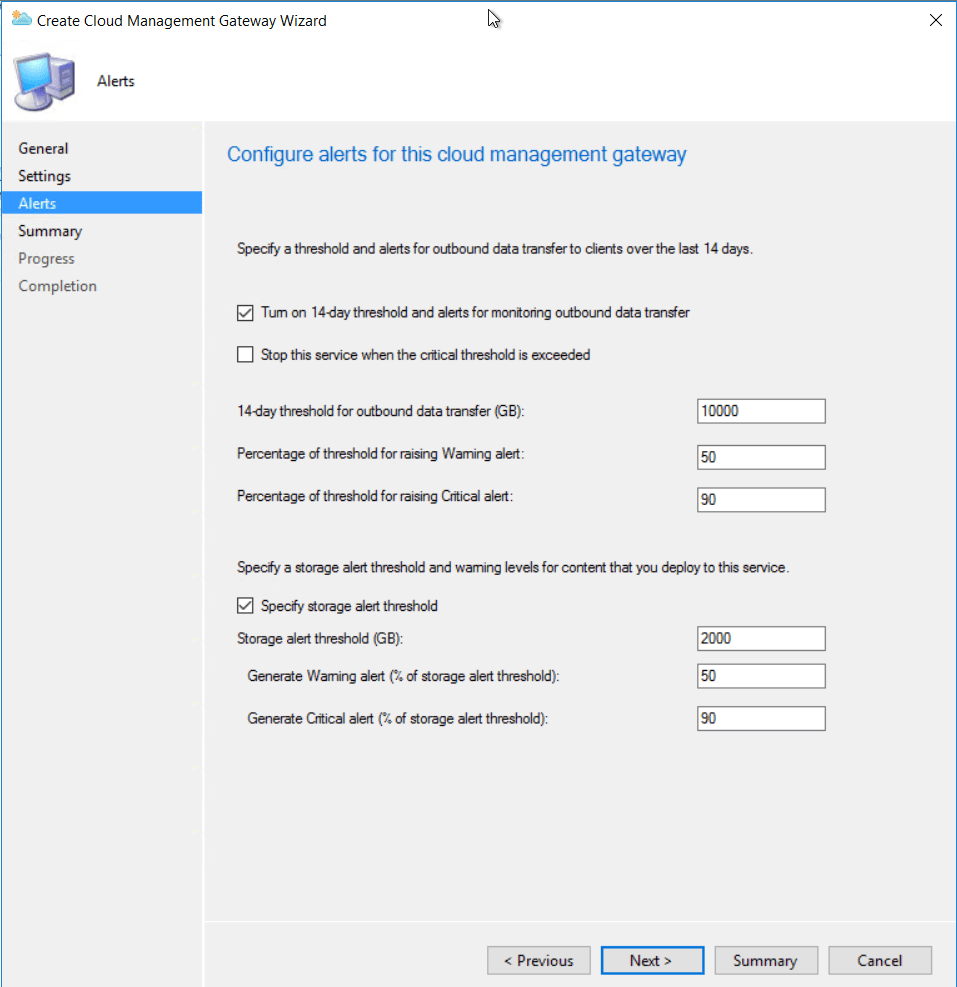 Just follow the wizard to complete.
Just follow the wizard to complete. 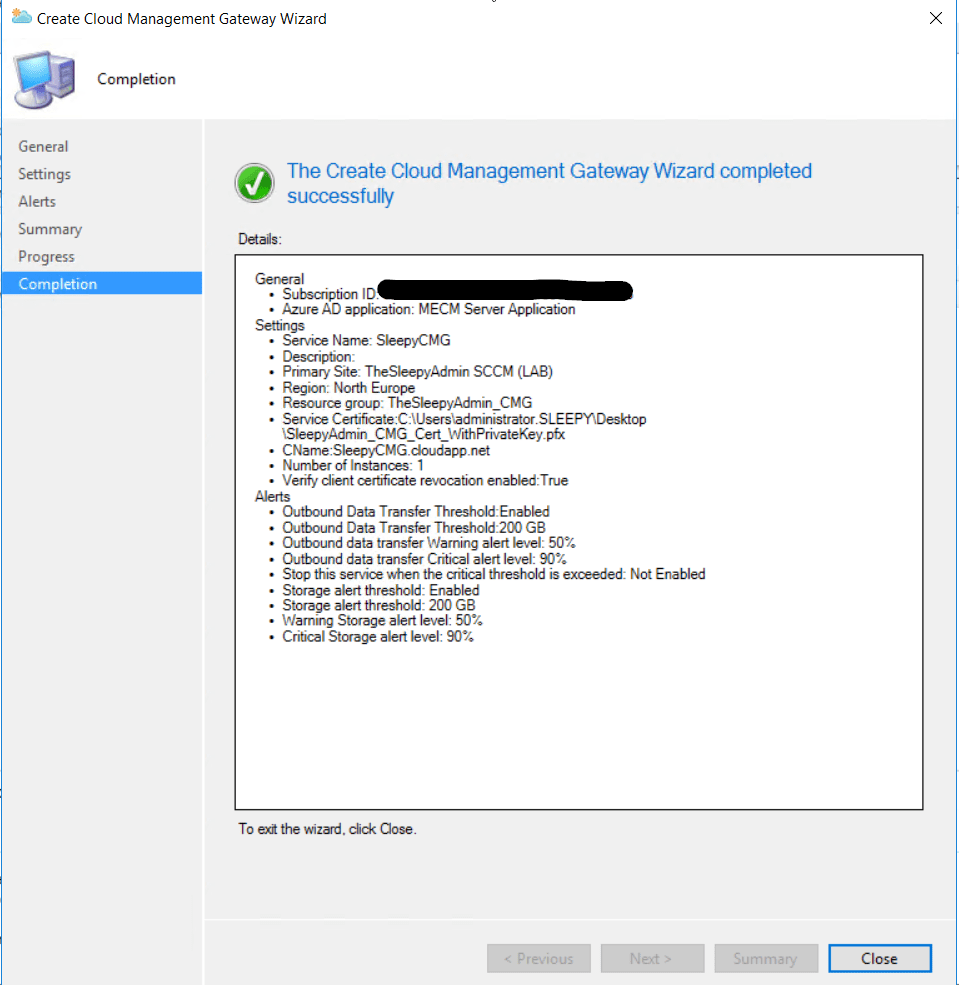
Once completed the CMG should show as provisioning started
We can also logon to Azure to verify the cloud service has been created. 
After the CMG has been configured we then need to install the Cloud management connection point to connect MECM to the CMG.
Go to Administration > site configuration > servers and site system roles, Add the Cloud management gateway connection point to the primary site server in MECM
After the role has been configured we need to configure a few steps on the site server, management point and software update point (if installed and configured)
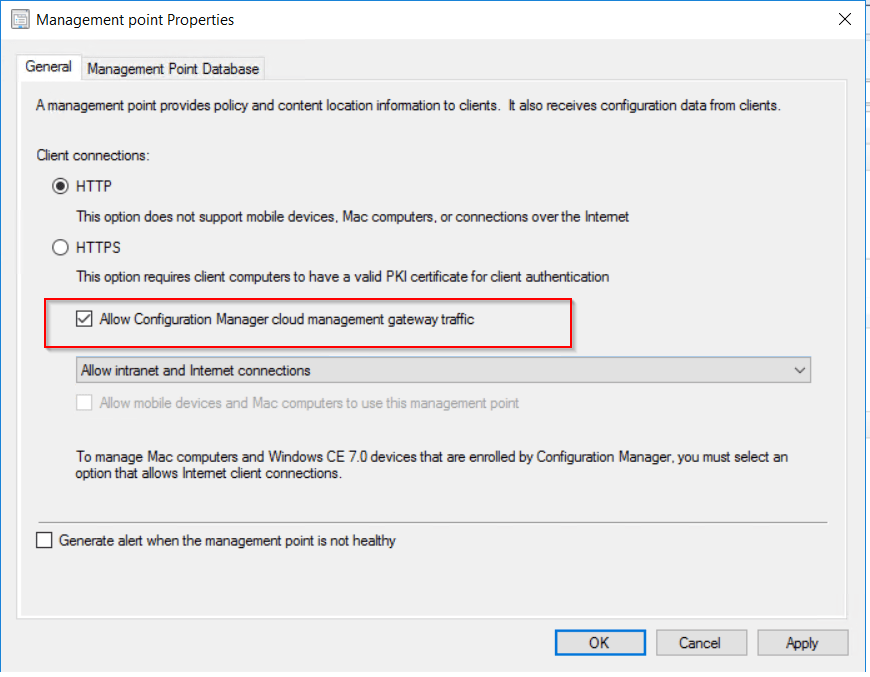
Open the management point properties and tick the allow configuration manager cloud management gateway traffic. (If the tick box for is greyed out there is an additional step required.)
Go to Administration > site configuration > sites, then configure the primary site to use configuration manager generated certificate in communication security. Once this is done go back to the management point and the tick box should now be available.
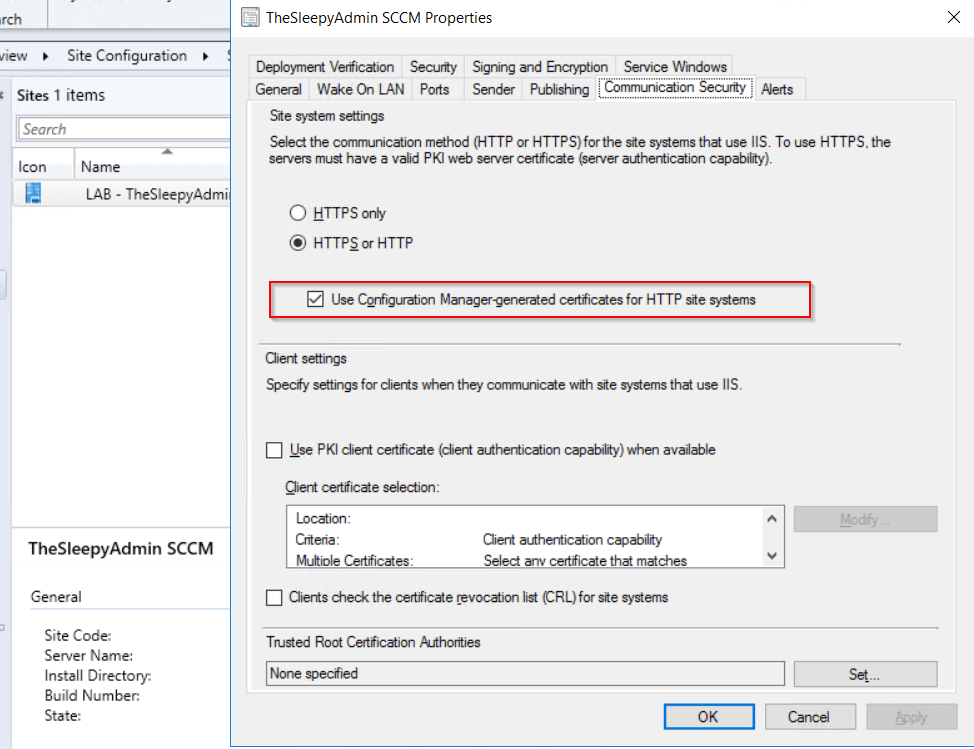
 To allow the software update point to communicate with the CMG, tick the allow configuration manager cloud management gateway traffic.
To allow the software update point to communicate with the CMG, tick the allow configuration manager cloud management gateway traffic. 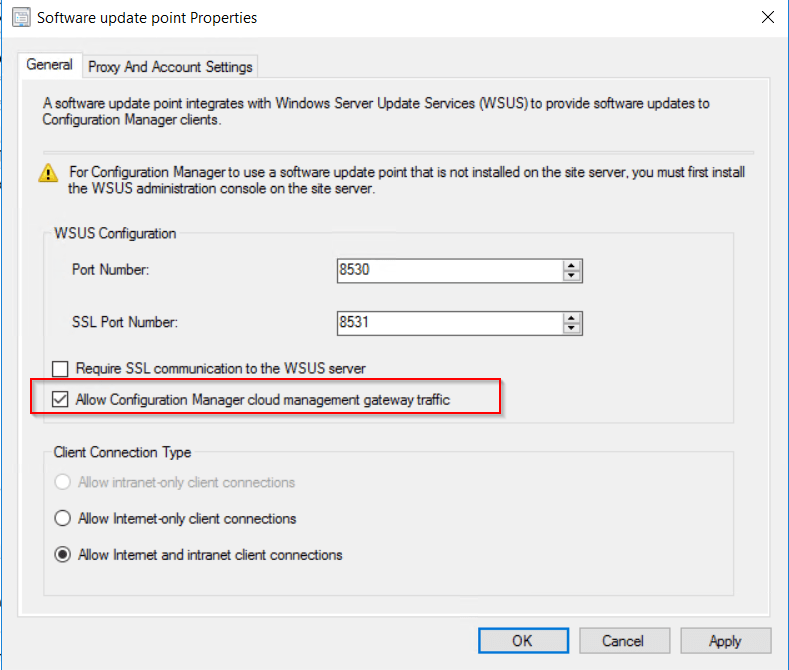 After this has been configured the clients should now pick up a the CMG as a internet based management point in the network tab of client agent properties.
After this has been configured the clients should now pick up a the CMG as a internet based management point in the network tab of client agent properties. 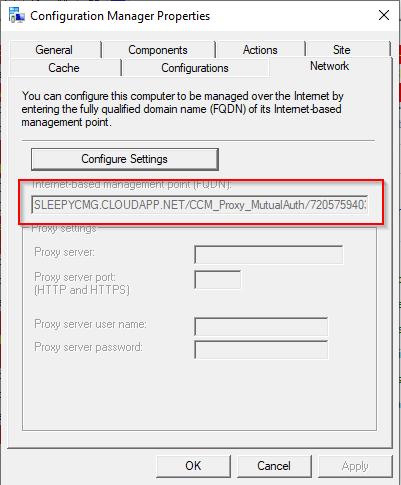
Once the client moves off the internal network and does a location lookup we should see that the connection type will change to internet from internal. 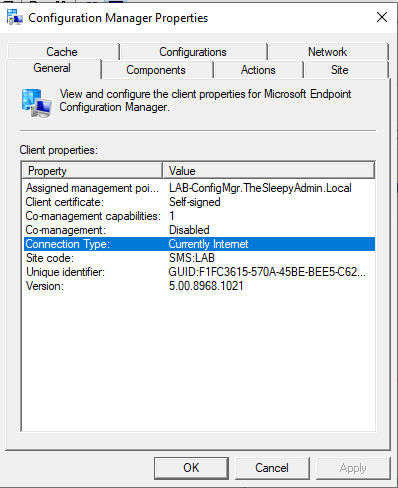
We can also check the location services log to see if the CMG is being picked up. 