During our recent Windows 10 feature update deployment from 1809 to 20H2, we ran in to an issue on some clients where they reported back error 0XC190012E to ConfigMgr.
The error code its self is just a generic code and I couldn’t find it in either
Windows update error code list
Windows Update error code list by component – Windows Deployment | Microsoft Docs
or the Windows 10 upgrade errors doc
Get help with Windows 10 upgrade and installation errors (microsoft.com)

We first checked the temporary location that feature update deploys to c:\$Windows.~BT, to check if there was any issue in the compatibility xml file or in the setup logs under sources\panther, but there was no folders other than sources.

Since there was no files I though this might be a space issue so ran some remote WMI commands to check the disk space available. I used the below PowerShell using Get-WMIObject.
Get-WmiObject Win32_logicaldisk -ComputerName RemoteComputerName | Select-Object @{Name="Drive";E={$_.DeviceID}},
@{Name="Size(GB)";E={[math]::Round($_.size/1gb)}},
@{Name="Free Space(GB)";E={[math]::Round($_.freespace/1gb)}},
@{Name="%Free Space";E={"{0:N2}" -f (($_.freespace/$_.size)*100)}}
In this case it wasn’t disk space a there was over 100GB free.
There wasn’t much online about the error other than the usually run scf /scannow, diskcheck and run the update troubleshooter but none of these worked.
Then found this post on the Microsoft forms that pointed to an issue with the setupconfig.ini
Generic 0xc190012e trying to upgrade Windows 10 1909 to 20H2 – Microsoft Community
C:\Users\Default\AppData\Local\Microsoft\Windows\WSUS

We aren’t using any custom setting in the setupconfig.ini so there was no issue for me to remove this.
Once I removed the file and kicked off the feature update again it now completes without issue.
I don’t know how the setupconfig.ini file was created on only a few devices but it was a quick fix once we found the issue was the config file.



















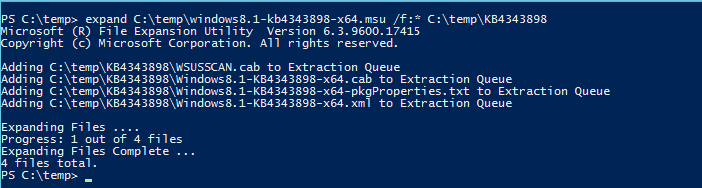 Once the update is extracted use Dism to add the problematic update this should install the missing files.
Once the update is extracted use Dism to add the problematic update this should install the missing files.