Recently we have been having an issue with VMware PowerCLI not passing through the users credentials when running Connect-viserver to connect to our vCenter servers.
This has been causing problems when trying to use scheduled task to automated reports and run remediation task like removing old snapshots or reporting on VMware Tools versions as it is prompting for credentials.
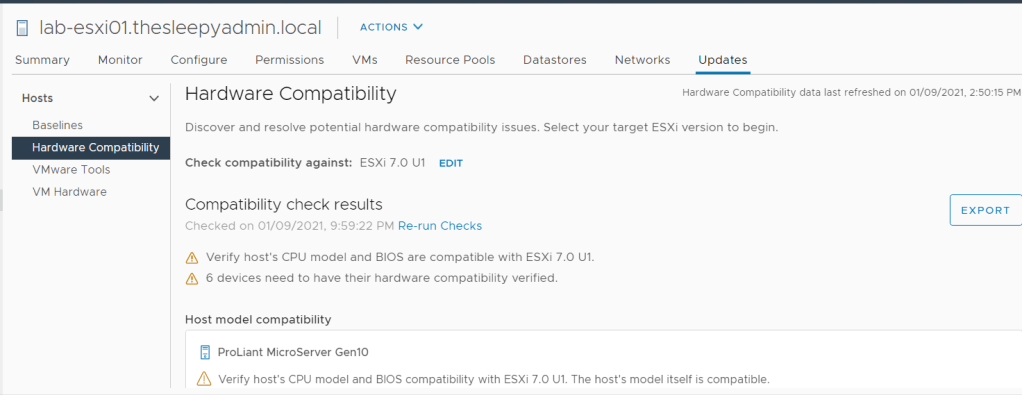
For integrated authentication to work, the vCenter servers needs to be setup to allow single sign on for the domain that you will be connecting from, so confirm that your Active Directory Identity source is added and that SSO works from the web client. If not, complete this first before trying to use PowerCLI with integrated authentication.
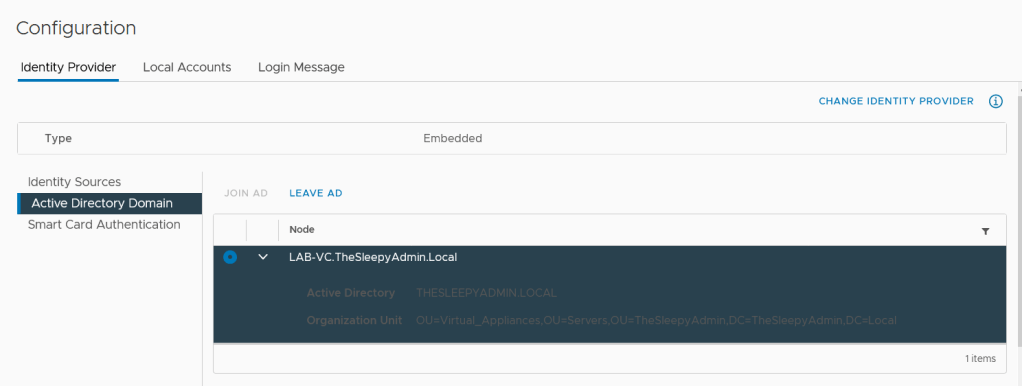
I have SSO configured and tested so this wasn’t my issue.
When using the older version of PowerCli version 6.5 and below we had no issue with integrated authentication and would connecting to vCenter server without prompting me for credentials.

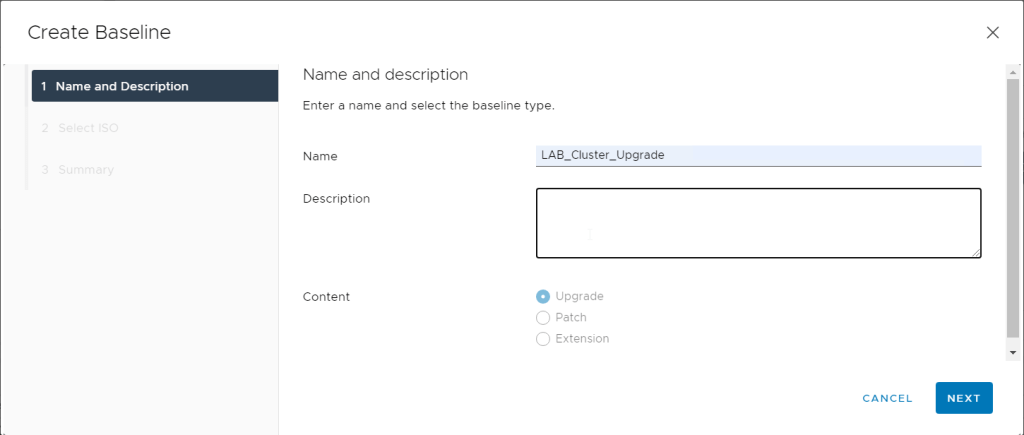
We could continue to use the old version of PowerCLI but we would be missing out on improvement and new commandlets so I wanted to try and get the newer version working for automated task.
First we install the VMware.PowerCLI module using Install-Module VMware.PowerCLI, the current version is 12.1

When I tried to connect using this version of PowerCLI I get prompted for a user name and password and this is what is stopping my automated task from running.

There are a few ways to workaround the prompt and this can also be used to confirm if SSO is working correctly. One way would be to add credential store item that can be used for connecting.
To add this use the VICredentialstore commandlet.
New-VICredentialStoreItem -User domain\username -Password Password -Host vc.domain.local -File C:\Temp\vicreds.xml
This outputs the credential to an xml file that can then be imported and called using Connect-VIserver.
$logon = Get-ViCredentialStoreItem -File C:\Temp\vicreds.xml
Connect-VIServer -Server $logon.Host -User $logon.User -Password $logon.Passwor
This works but I don’t really want to have a xml file that has information saved to it and someone might remove the folder or file by mistake.
The other way would be similar but using a txt file with the converted to a secure string password but again this relies on a file which is not ideal and not really all that secure.
The last option and one that I wouldn’t recommend at all is to hard code a username and password in the script.
So now that we have gone through some work arounds I decided to have a look at the actually problem .
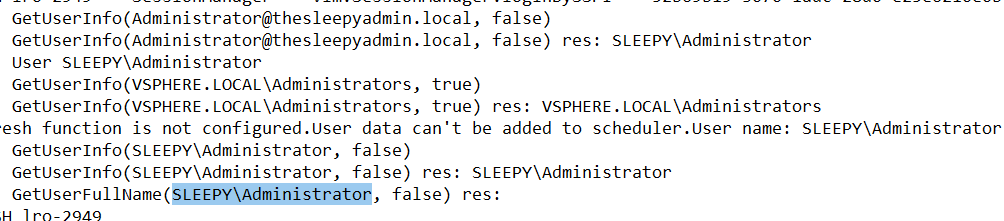
The above proves that authenticating against AD is working so I knew it wasn’t an account or SSO issue so it had to be an issue with PowerCLI itself.
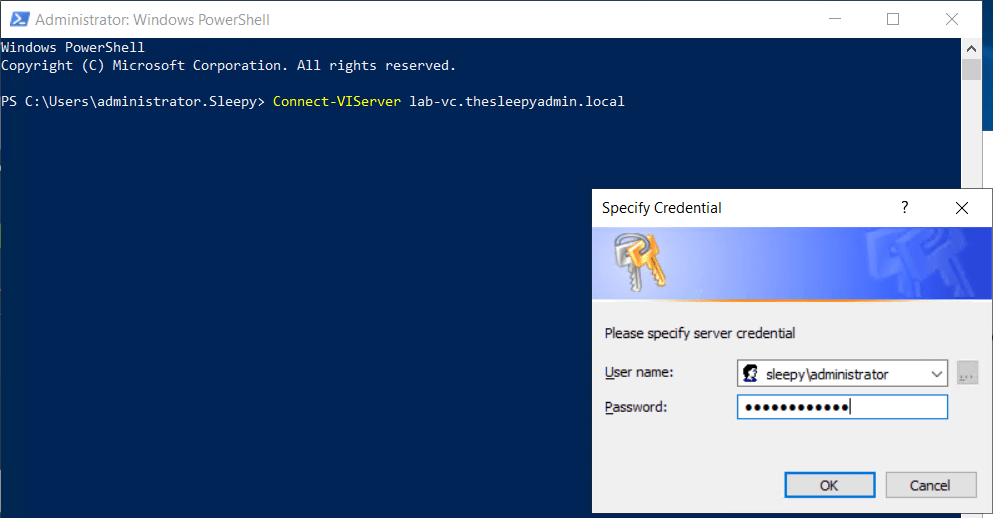
I connect using a my user name and passwords and it connect without issue.
I then check the VPX log under /storage/log/vmware/vpxd to see if there are an issue but I didn’t see any issues.
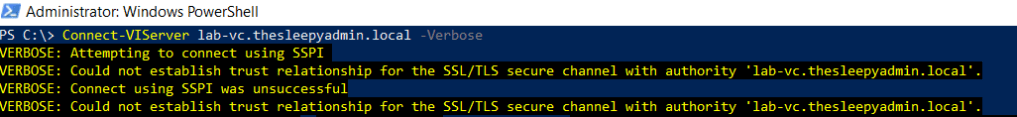
Next I tried to use the -verbose parameter to return more information on what exactly connect-viserver was doing,
This then returned an error for TLS.
I next checked the settings on PowerCLI configuration settings.
To check the PowerCLI configuration use
Get-PowerCLIConfiguration
When checking the configuration the Invalidcerificaeaction was set to unset.
I changed this setting to warn instead of unset
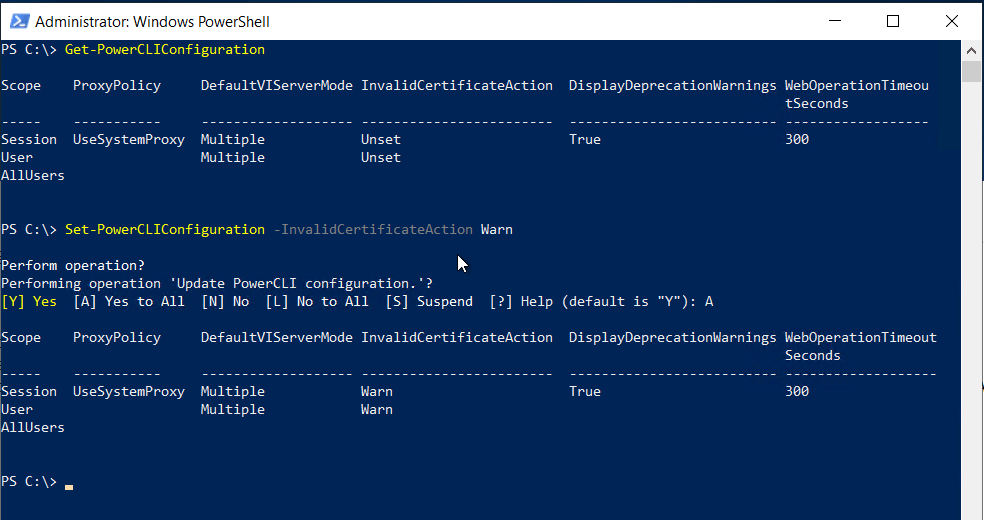
Once this setting was changed I can now connect to PowerCLI with integrated authentication, I do get a long warning message though I could set this to ignore and this returns no warning or error.
There are two ways around this instead of changing the above setting. One is to install the the certificate as a trusted root certificate so that the cert is trusted.
Or if you have an internal certificate authority you to replace the default VMware cert with an internal cert.

Once this is done the connection work without requiring manual intervention and my automated scripts can be run using scheduled tasks again with the latest version of PowerCLI. Hopefully this will be helpful to anyone else having this issue.