We have been using LAPS for the last year or so and for the most part it is a great tool for managing local admins password.
In our environment we have multiple forest with trusts relationships and the one main issue that we have is that the LAPS UI client can’t check the local admin password of devices in other domains, unless we logon as a user in that domain and run the LAPS UI as that user.

We can use PowerShell but this requires either the commands to be run from a devices in the domain with the LAPS PowerShell module or can be done using remote ps session but this is not something everyone on the service desk would know how to do or will have rights to do.
Enter-PSSession dc.domain.local
Get-AdmPwdPassword -ComputerName "computer" | Select-Object Password,ExpirationTimestamp
We could also get the AD attributes by using get-adcomputer comandlet but this requires the AD PowerShell module.
Get-ADComputer -Identity "computer" -Server "DC" -properties ms-mcs-admpwd,ms-mcs-admpwdexpirationtime | select-object ms-mcs-admpwd,ms-mcs-admpwdexpirationtime
I wanted to try create a script that would allow them to check the other domains without the needing to know how to do PS remoting or having modules installed.
To get around using the AD module we will be using ADSI search instead as this a default part of PowerShell. I used the below blog to get started.
To query the remote doamin using adsisearch we first need to have a way of converting the domain name to the format that adsisearch requires.
This can be done using DirectoryContect class
System.DirectoryServices.ActiveDirectory.DirectoryContext
System.DirectoryServices.ActiveDirectory.Domain
DirectoryContext Class (System.DirectoryServices.ActiveDirectory) | Microsoft Docs
The first part of the script gets the domain details and returns the objects back to the search variable.

Next part we will filter the results based on the client variable to return only the required computer details.

Once the script is working, I just needed to create some mandatory parameters and create a function called Check-LAPS so that it’s easier for people to use without having to hardcode anything in the script and has some help and examples.

Below is the link to the full script.
Scripts/ActiveDirectory/LAPS at master · TheSleepyAdmin/Scripts (github.com)
Below shows how the script is run and the results.

I used the above script with WPF to create a GUI that is now complied in to an exe. I though this would be a lot easier to pass on the service desk as all they need to do is run the exe.
This was compiled using ps2exe PowerShell module.
MScholtes/PS2EXE: Module to compile powershell scripts to executables (github.com)

All they need to do is put in the domain name and computer name.

This should then return the LAPS password.

I will do a different post on creating the GUI itself in as this was my first GUI and I would like to create a few other.
 Password settings policy used to set the password complexity, length and age
Password settings policy used to set the password complexity, length and age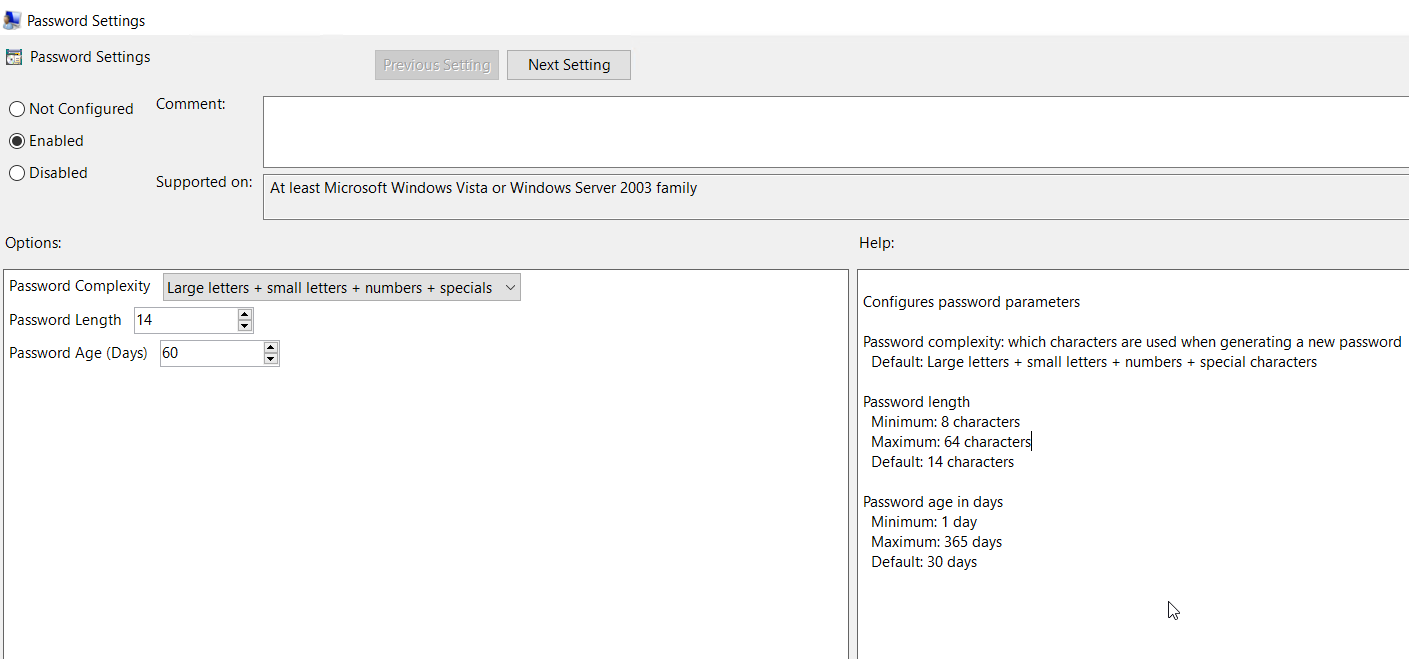 Specify the account that the password policy will apply to if this is the default administrator account this should be left at default
Specify the account that the password policy will apply to if this is the default administrator account this should be left at default
 Enabled management of local admin account
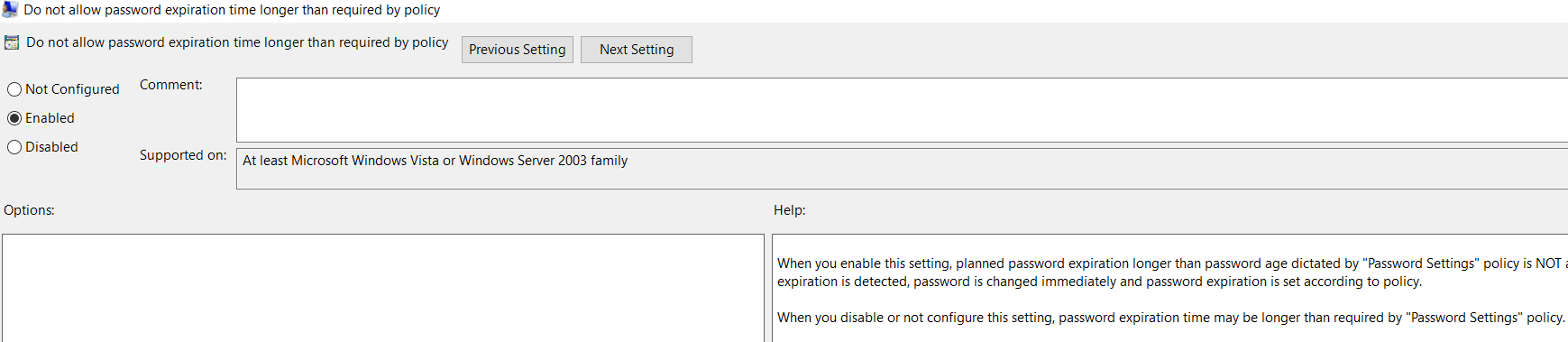
Enabled management of local admin account Once the policy is configured apply the policy against the required OU
Once the policy is configured apply the policy against the required OU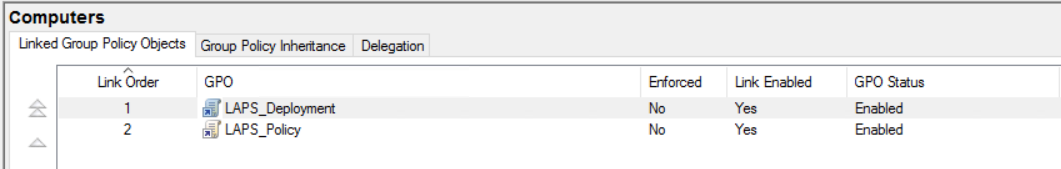 To confirm that all settings are working, run a gpupdate on a test device. Once applied we can check the password in a few different ways
To confirm that all settings are working, run a gpupdate on a test device. Once applied we can check the password in a few different ways



 There are two command to set the rights, one for read and one for reset rights
There are two command to set the rights, one for read and one for reset rights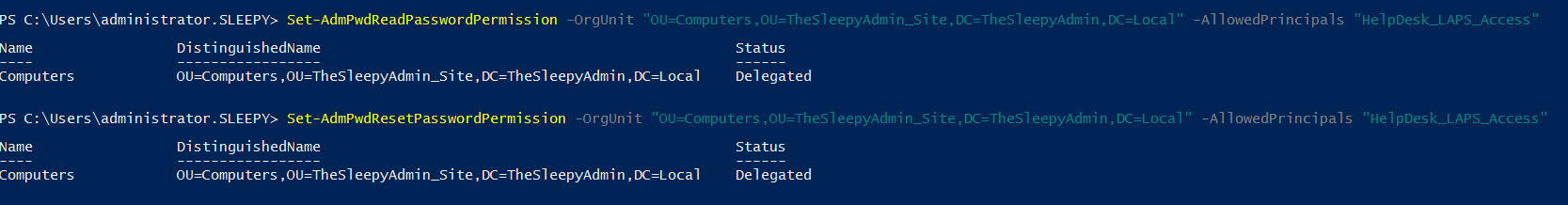 Last step is to verify the permission have been applied
Last step is to verify the permission have been applied
 Add the installer
Add the installer

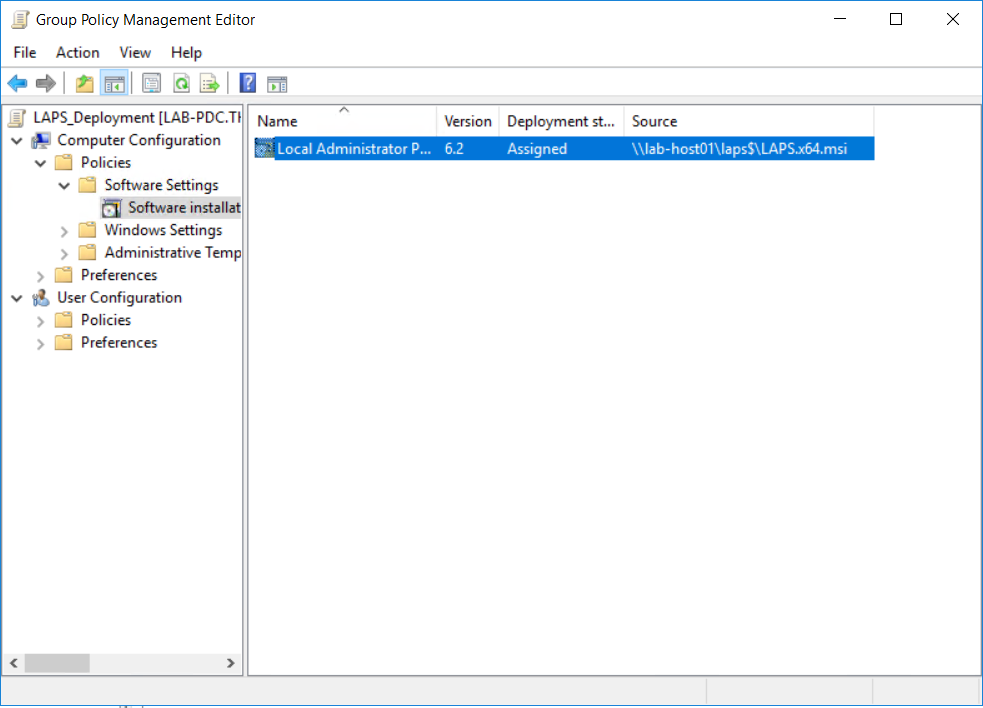 Next apply the policy agaist the OU or use security filtering to apply to specific devices once the policy is applied logon to the device and run gpupdate /force to apply
Next apply the policy agaist the OU or use security filtering to apply to specific devices once the policy is applied logon to the device and run gpupdate /force to apply 









