In this post we will be going through configuring Network Security Group’s to restrict access between subnets under a single vNet.
Routing between subnets happens automatically and is allowed by default.
This can allow resources communicate over any port and there is no network access control.
To make the Azure network more secure this should be restricted as much as possible to only allow the required communication.
Below is a link to the Microsoft network best practice.
One way to limit the communication is to use NSG’s.
In this example we will be using a 10.10.1.0/24 address space

Then we will be creating multiple subnets with /28 mask.

I have added one server to both the Ops and Mgmt subnets. Now if we make a connection between each VM the traffic will be routed directly between both VM’s.

Next, we will setup the NSG to only allow connection between the subnets for RDP and SMB. In this case we will be creating an NSG per subnet, but this could be done in one NSG.

Next, we need to create two new inbound rules one to allow the required ports and the second to deny all other access.
Go to inbound rules and select Add.

Added in the required details
· Source: IP Address
· Source Port:
· Destination: IP Address
· Destination IP Address:
· Service: Custom
· Destination Port Ranges:
· Protocol TCP
· Action: Allow
· Priority: 110
· Name: Allow_Mgmt_Subnet_Access

Next, we will create the deny rule.

I would usually set the deny to a much lower priority, so that if more rules are required in the future there won’t be an issue with the deny rule having a higher priority and blocking the traffic.
Once saved, the allow and deny rule should show under inbound rules.

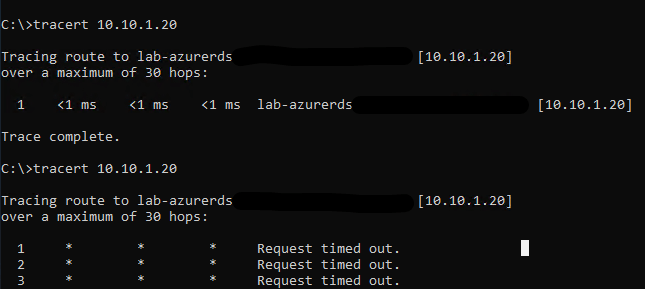
Now when we try to run tracert again, this time we won’t be able to connect.
If we try open a connection using SMB, we can connect without issue.

To block access back to the other subnet we will need to create the same rules but with the opposition subnet source and destination IP ranges.

After creating both set of NSG rules there will be no access between the subnets on any port other than those specified in the inbound rules.