During a recent Windows Defender deployment we ran in to an issue with the onboarding script where the Windows Defender feature would fail to install with Enable-WindowsOptionalFeature : The referenced assembly could not be found.

When checking the the CBS log under C:\Windows\Logs\CBS\CBS.log we found that the issue was related to a missing package for a previously installed update.
CBS Failed to pin deployment while resolving Update: Package_8092_for_KB5005043~31bf3856ad364e35~amd64~~10.0.1.3.5005043-16635_neutral from file: (null) [HRESULT = 0x80073701 – ERROR_SXS_ASSEMBLY_MISSING]
After a bit of troubleshooting there where two fixes to this issues, if the update that is missing is available, we can download the update MSU / CAB file from the Microsoft update catalog using the KB ID. I have covered this in a previous blog post so wont go over that fix on this post use the below link to view that post.
In some of our case the update file was not available to download any more, in this case we need to modify the registry to set the package values that are corrupted to be ignored.
Doing any modification of the registry comes with risk and this should only be done when all other solution have been attempted. Make sure there is a valid a backup before attempting this fix.
First we need to get the list of packages that are showing in the CBS logs as corrupted. The below script will go through the CBS log and get the packages and format the results.
$cbsLog = "c:\windows\logs\cbs\cbs.log"
$results = @()
Write-Host "Checking CBS logs for SXS Assembly Errors" -ForegroundColor Green
$checkingfailure = Get-Content $cbsLog | Select-String "ERROR_SXS_ASSEMBLY_MISSING"
$cbsresults = Get-Content $cbsLog | Select-String "Resolving Package:"
if ($cbsresults) {
foreach ($cbsresult in $cbsresults) {
$packageresult = ($cbsresult | Out-String).Split(":").trim().Split(',')| Select-String "Package_"
$results += $packageresult
}
}
$results | Select-Object -Unique

Now that we have the list we need to set the local administrators group as the owner of the component registry key in order to be able to update the effect packages current state so they wont be checked.
Open regedit and go to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing

Select Administrators as the owner and replace owner on subcontainters and objects.

Last step is to set the local administrators with full control of the registry key.

Now that we have the permissions set we can modify the registry values. This can be either scripted or manually done.
The current value needs to be change to 0 to set.


Set each of the corrupted package to 0
Then revert the permission back so Administrators have read access and trusted installer (NT Service\TrustedInstaller) is the owner of the components registry key and subkeys.
Now when we try and run the onboarding script again the Windows Defender feature enables without issue.























































 Once the workspace has been created we need to configure the on-premises connection account.
Once the workspace has been created we need to configure the on-premises connection account. 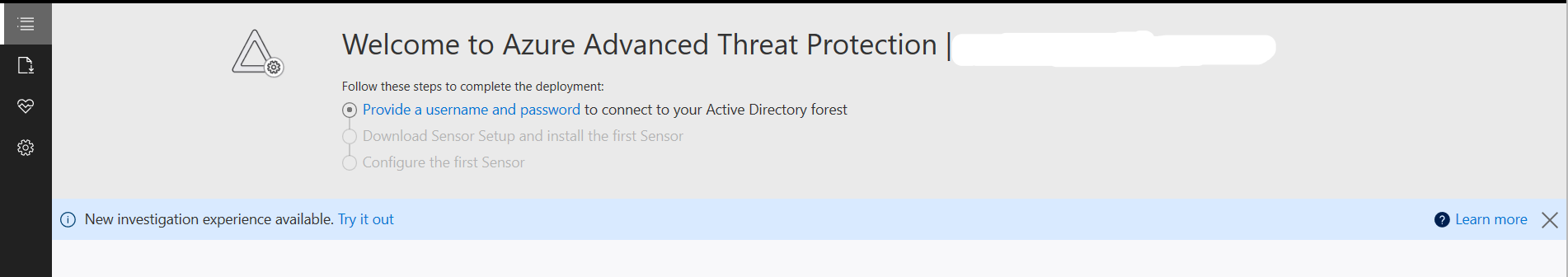 Put in details for the domain account, I used a service account that has read access to AD so that I could restricted the logon to the account to only be used for ATP
Put in details for the domain account, I used a service account that has read access to AD so that I could restricted the logon to the account to only be used for ATP 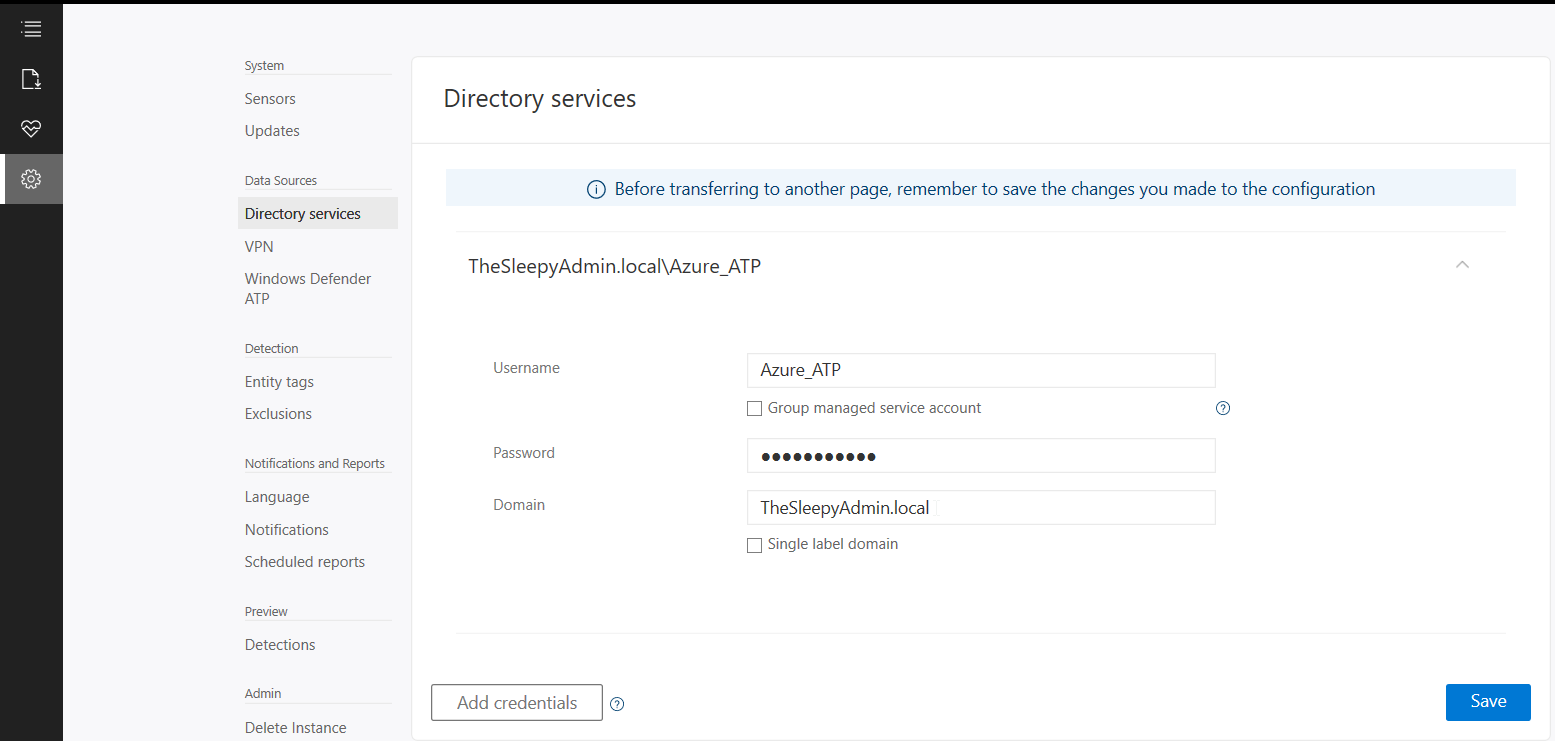 Once AD details are added next step is to download and install the sensor agent. Go to sensors and download the setup exe and copy the access key as this will be required during the install.
Once AD details are added next step is to download and install the sensor agent. Go to sensors and download the setup exe and copy the access key as this will be required during the install. 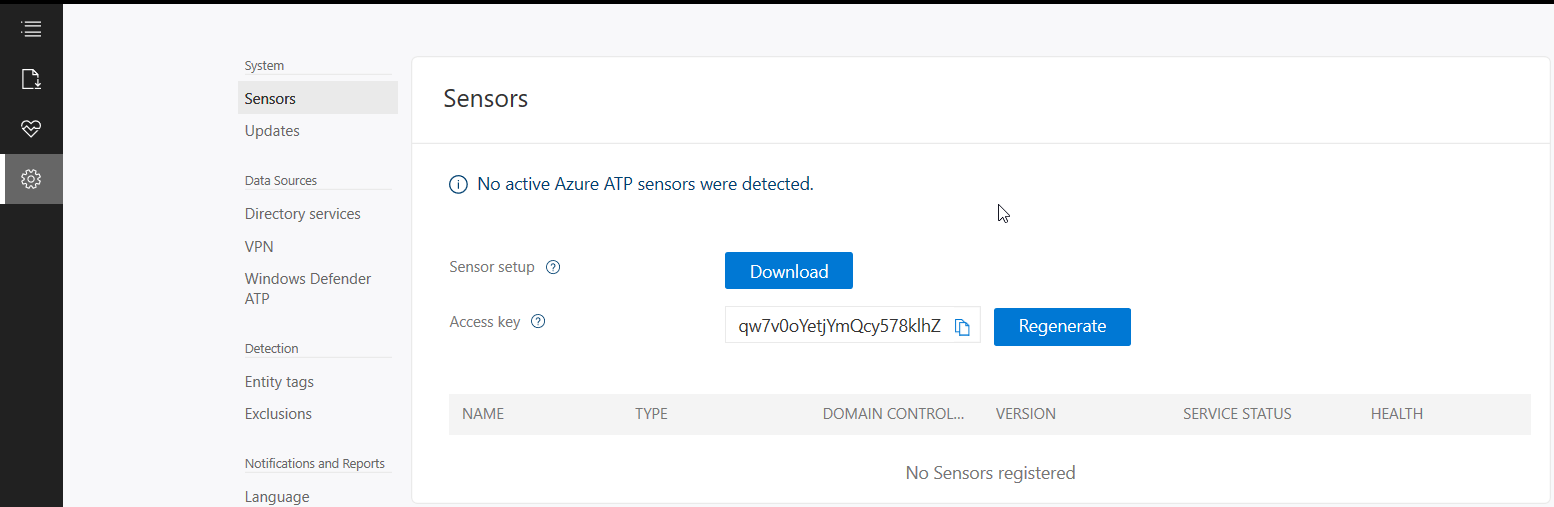 Copy the installer to the DC and run.
Copy the installer to the DC and run.  Select required language.
Select required language.  Deployment type will be sensor I am running on VMware and this will generate the below warning which will redirect to a guide to disable IPv4 TSO Offload.
Deployment type will be sensor I am running on VMware and this will generate the below warning which will redirect to a guide to disable IPv4 TSO Offload. 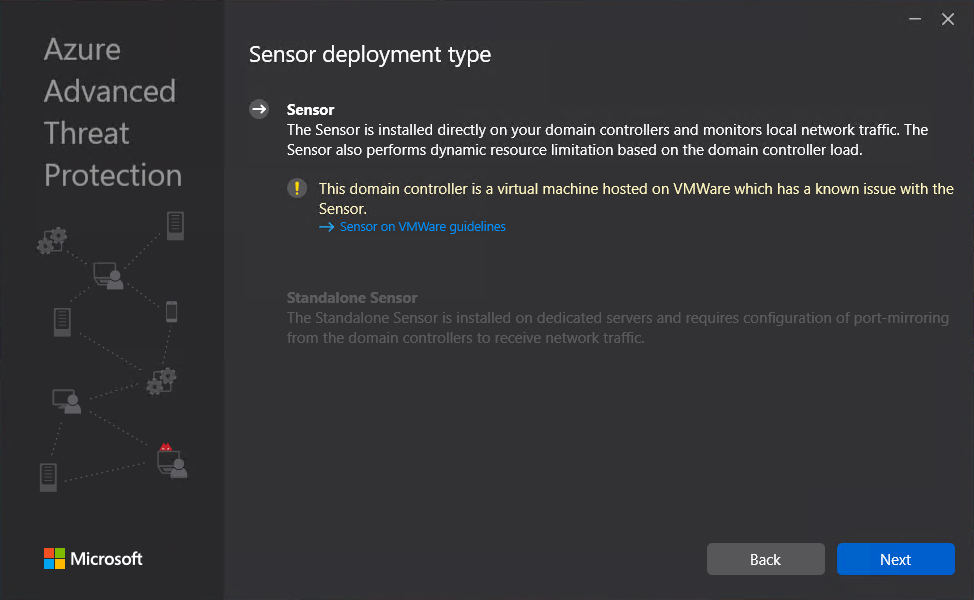 This is where we need to put in the access key so that the sensor is associated to the correct workspace.
This is where we need to put in the access key so that the sensor is associated to the correct workspace. 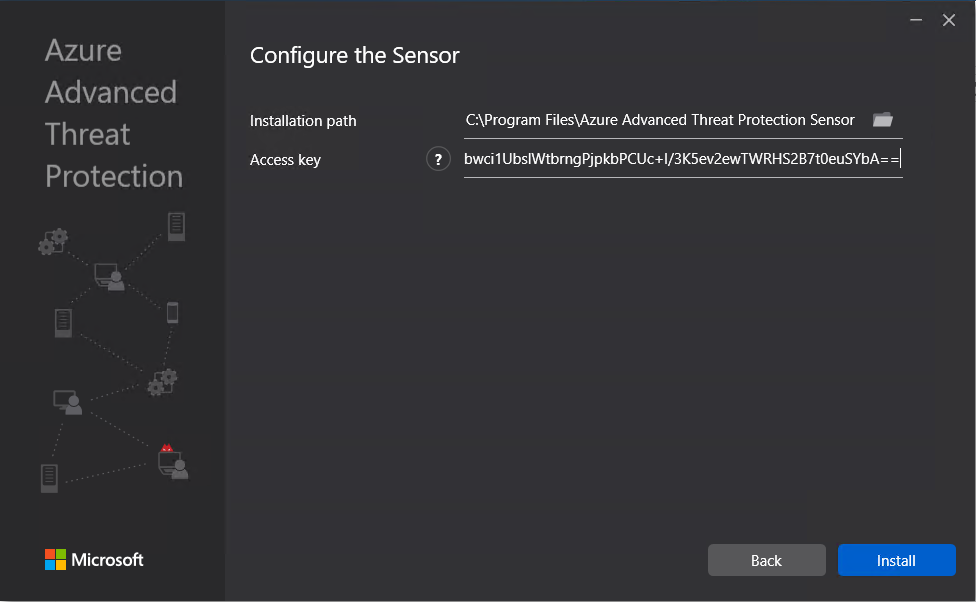 The agent should now start to install.
The agent should now start to install. 
 Once the agent has install it can take some time for it to respond in Azure ATP.
Once the agent has install it can take some time for it to respond in Azure ATP. Now the agent should start to notify of any suspicious activity that run’s like reconnaissance on SMB, DNS and other malicious reconnaissance.
Now the agent should start to notify of any suspicious activity that run’s like reconnaissance on SMB, DNS and other malicious reconnaissance. We can also add sensitive account and group, there are default groups/ accounts that are considered sensitive by default like Administrators, Domain admins, Enterprise admins…, a full list of these can be found in the below link.
We can also add sensitive account and group, there are default groups/ accounts that are considered sensitive by default like Administrators, Domain admins, Enterprise admins…, a full list of these can be found in the below link.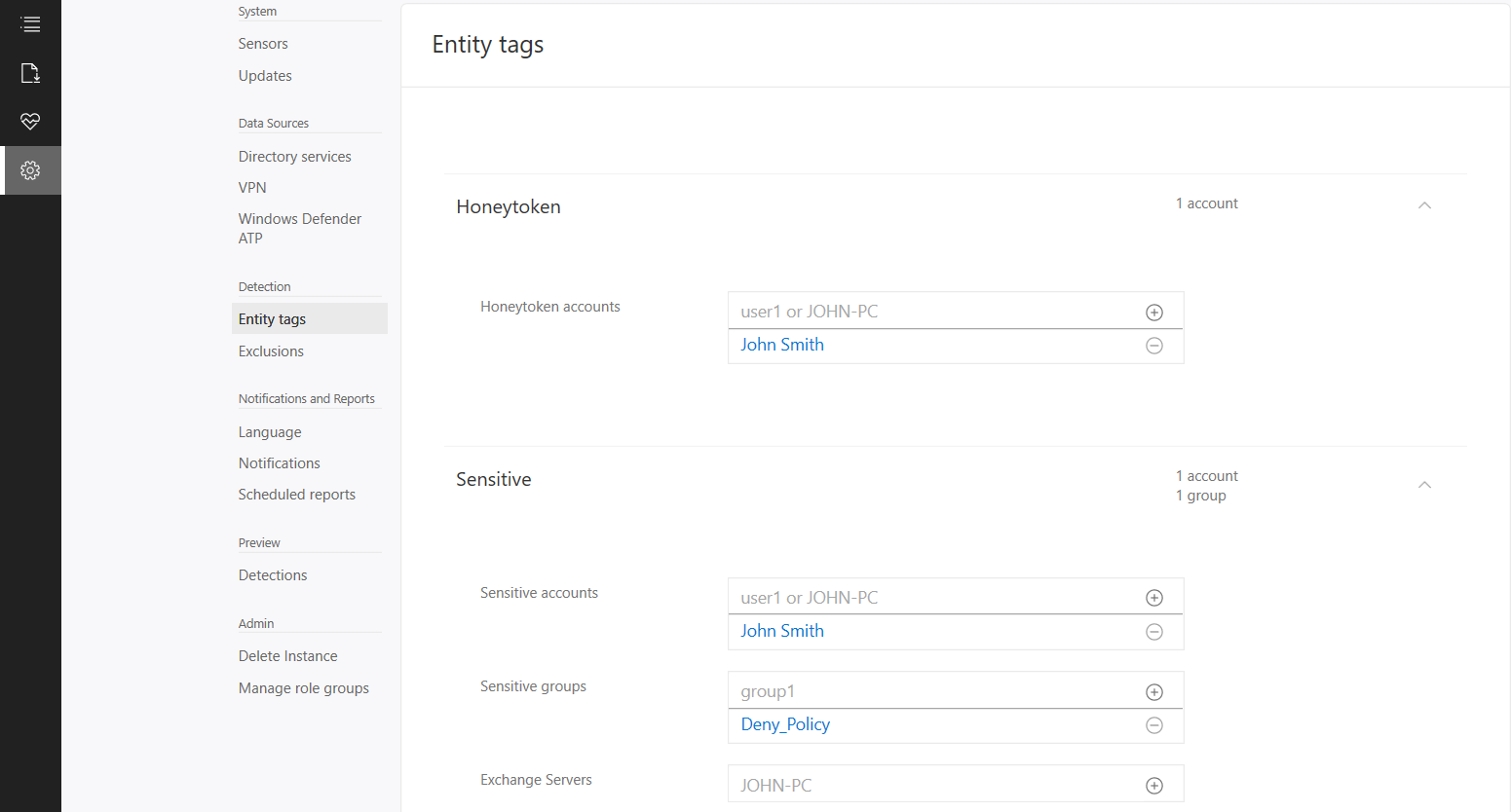 If we now logon with the HoneyToken account it will then alert the activity by this account.
If we now logon with the HoneyToken account it will then alert the activity by this account. 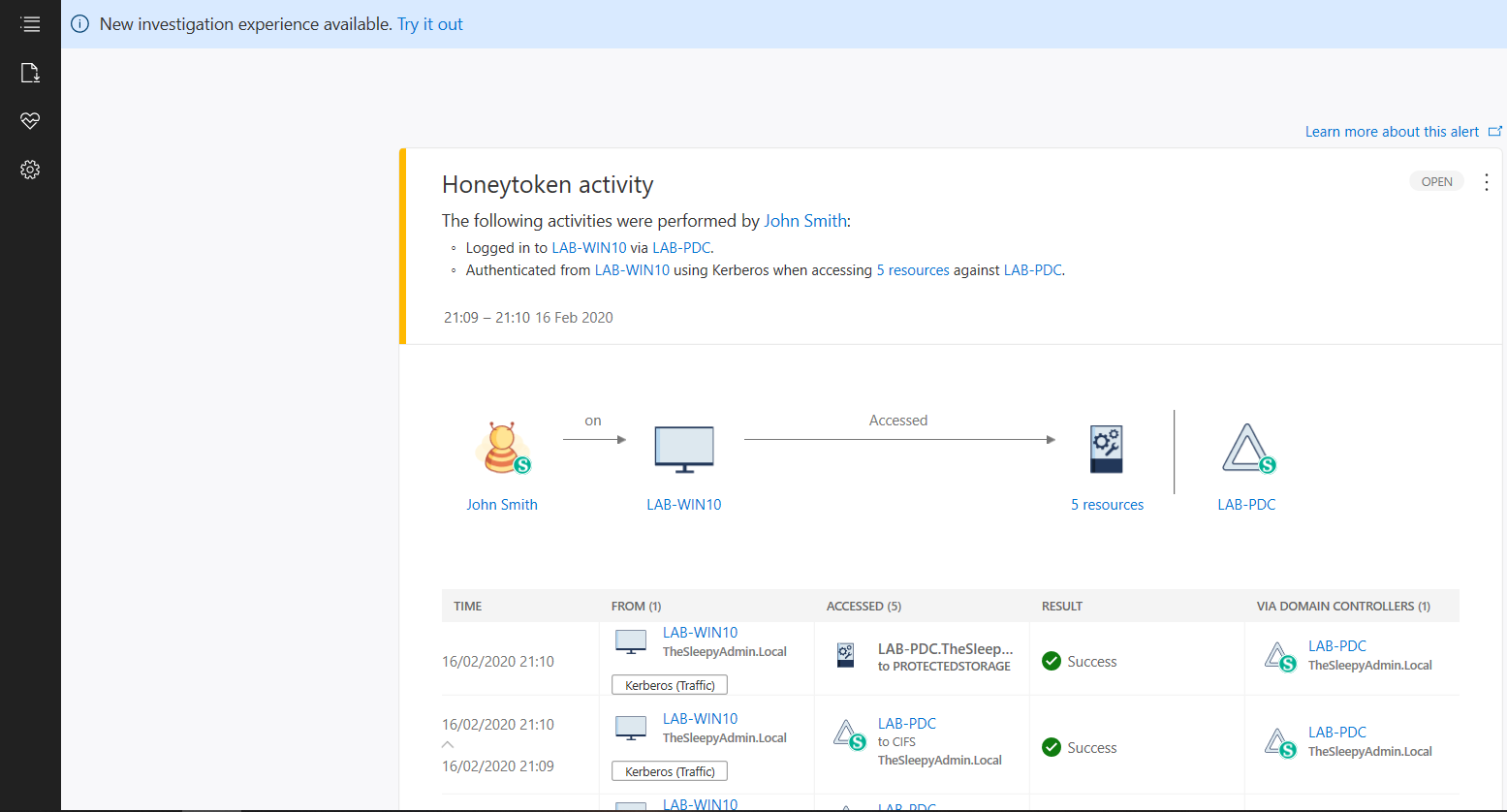 We can also run reports or schedule reports for schedule reports. To run a report go to the reporting blade and change the date to the range you want and click download.
We can also run reports or schedule reports for schedule reports. To run a report go to the reporting blade and change the date to the range you want and click download. 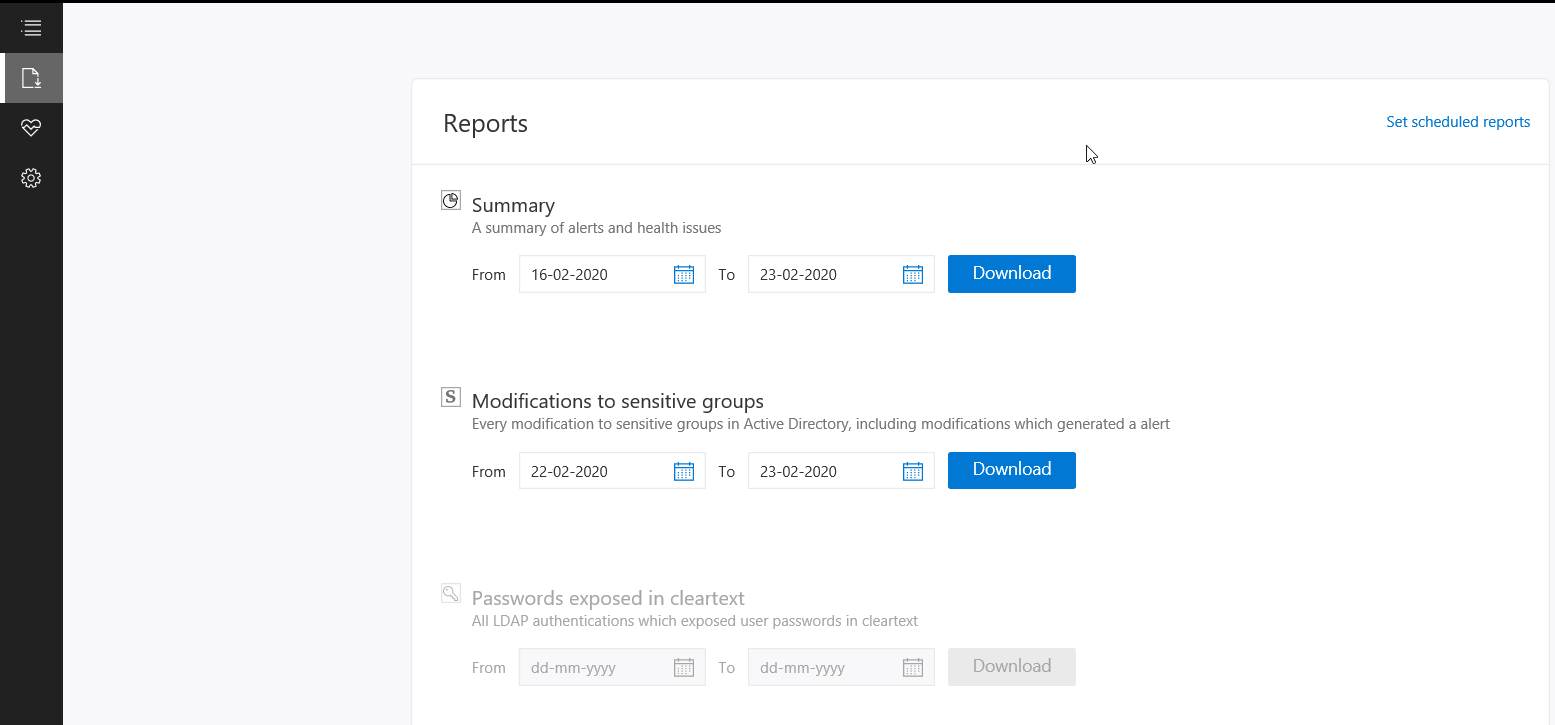 Below is an example of the modification to sensitive groups.
Below is an example of the modification to sensitive groups. 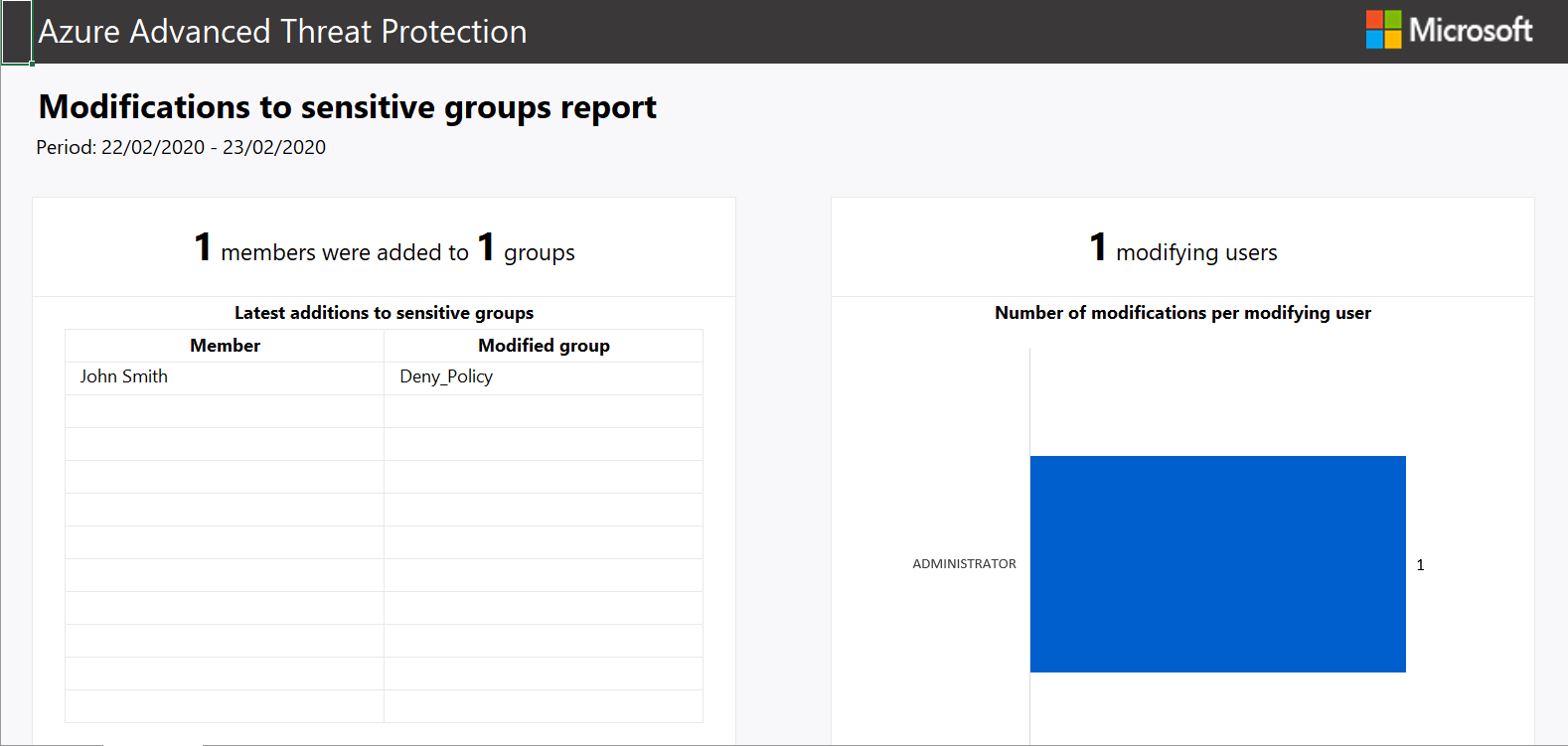 To scheduled reports go to configuration and scheduled reports.
To scheduled reports go to configuration and scheduled reports. 





















