In this post we will be going through setting up a conditional access policy to allow connection’s to a Microsoft App Registration that will be used for calling Microsoft GraphAPI from only certain countries / public IP’s.
Microsoft has a preview feature in Conditional Access for workload identities. A workload identity is an identity which allows an application or service principal access to resources.
When an App Registration is created, it will create a service principal. This service principal is what we will use in the conditional access policy.
First we need to create the named location to define where we want to allow the access from.
To create a named location go to endpoint management admin page.
https://endpoint.microsoft.com/
Go to Endpoint security > Conditional access.

Once in Conditional access, go to Named location and add the required countries locations and or IP ranges.

To add as single IP use /32 bit subnet mask.

Once we have the named locations we can create the Conditional access policy.
Go to the policies tab and click on new policy.

Give the policy a name and set the assignment to workload identities.

Next select the service principal for the Graph App registration.

Next on Cloud apps or actions select, All cloud apps

Next we need to specify which location will be included, which we set to any location as we will use the exclude to allow access from the named location we will connect from.

Next select the location that will be excluded from the policy in my case it will be the public IP we added earlier to the named location.

Next we set the access, I will be blocking access as I only want to allow access from the one public IP we specified in the excluded location.

With any conditional access policy I would recommend setting the policy to Report-only to confirm that only the access that we excepted to be blocked is.

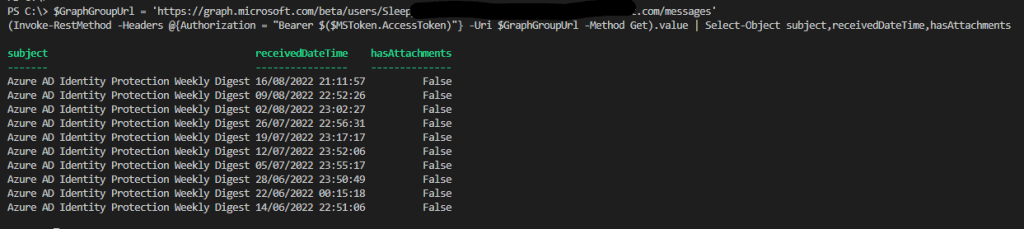
To check if the policy is applying correctly against the service principal we can check the sign-in logs.
First connect using Graph query and then go to sign-in logs.

Select service principal sign-ins.

Click on the request ID and look at the Report-only tab to see if the access would have been blocked or allowed.

Once we confirm that the policy is applying the correct access, the conditional access can be set to on.

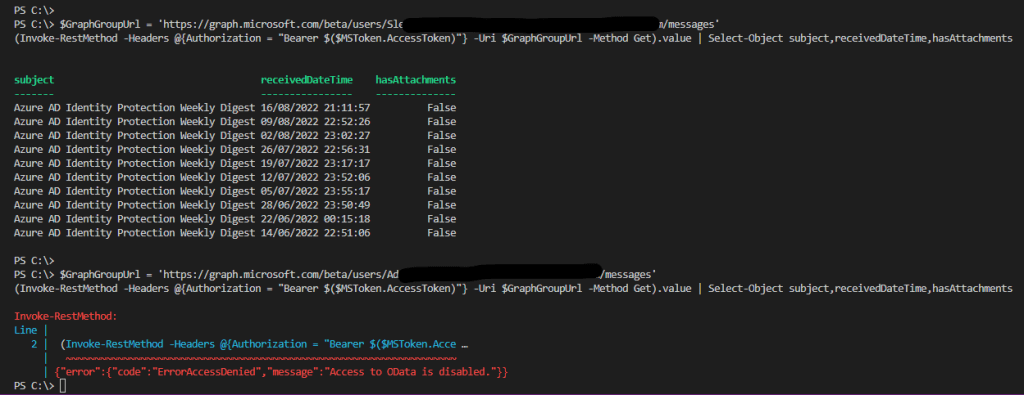
Now once we try to connect from an IP or location not on the excluded list, it will be blocked from accessing.

When we connect from an allowed location, we will get back the access token and be allowed to connect.

When creating App registration we should look at access controls for these as this can be over looked and lead to a security risk, most application do not need access from any location and should be limited to only the require location or IP address to give greater access control.