In this post we will be looking at creating a report to show what Azure App registrations have expiring client secret / certificate in the specified amount of days.
There is currently no in built way to report on expiring App registrations in the Azure portal other than checking the app registration, so we will be using Microsoft Graph SDK to automate the reporting.
First to automate the report we need to create an app registration to use for the Microsoft Graph connection. I have gone through this in a previous post.
The specific Microsoft GraphApi application permission required is Application.Read.All, this needs to be added to the App Registration that we use for Microsoft Graph.

Next we need to connect to Microsoft Graph using.
Connect-MgGraphTo list the app registration use
Get-MgApplication
Once we have the list of apps we can use PasswordCredentials to view client secret details
(Get-MgApplication).PasswordCredentials
and KeyCredentials to view the certificates details
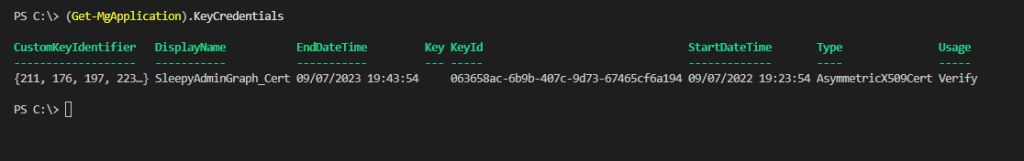
Once we have the required properties, we can create the script to export the app registration details.

There are two parameters Reportonly which returns just the result to PowerShell window and ReportExport which will export the report to the specific folder specified.
Below is what the Reportonly should look like.
.\Get-AppRegistrationDetails.ps1 -CertificateThumbprint Thumprint -ClientId ClientID -TenantId TenantID -ReportOnly -ExpiryDate 200
When using the Reportexport
.\Get-AppRegistrationDetails.ps1 -CertificateThumbprint thumbprint -ClientId ClientID -TenantId TenantID -ReportExport C:\temp\Graph\ -ExpiryDate 200
The full script can be downloaded from the below GitHub link.
Great Script, but only gets the certs and certificates for app registrations.
How do we get the same info for enterprise apps?
LikeLike
Hi Kim
Would you have an example that I could check, and I could update the script if needed. I think the certs are only when you setup SSO for the Enterprise app but I have not looked at this yet.
LikeLike
Hello, certs in enterprise apps are used for example when you want single sign on.
I managed to use your script as a template and create a separate script that creates a report for the certs used in the enterprise apps and the expiration dates.
Sorry for the late reply, I had some trouble with getting the correct data in the script.
The script uses the cmdlet called “Get-MgServicePrincipal” to get all enterprise apps along with the certinfo as well. I posted the portion of the script that gets the info below.
$EnterpriseApps = Get-MgServicePrincipal -All
$EnterpriseApps_ExportInfo = $EnterpriseApps | ForEach-Object {
[PSCustomObject] @{
AppDisplayName = $_.DisplayName
EndDateTime = $_.PasswordCredentials.EndDateTime
CertName = $_.PasswordCredentials.DisplayName
AppEnabled = $_.AccountEnabled
ObjectID = $_.Id
AppId = $_.AppId
Type = $_.GetType().name
Ägare = $_.Owners
Notes = $_.Notes
AppCreatedTime = $_.AdditionalProperties.createdDateTime
NotificationEmailAddresses = $_.NotificationEmailAddresses
LoginUrl = $_.LoginUrl
ReplyUrls = $_.ReplyUrls
Description = $_.Description
}
}
LikeLike