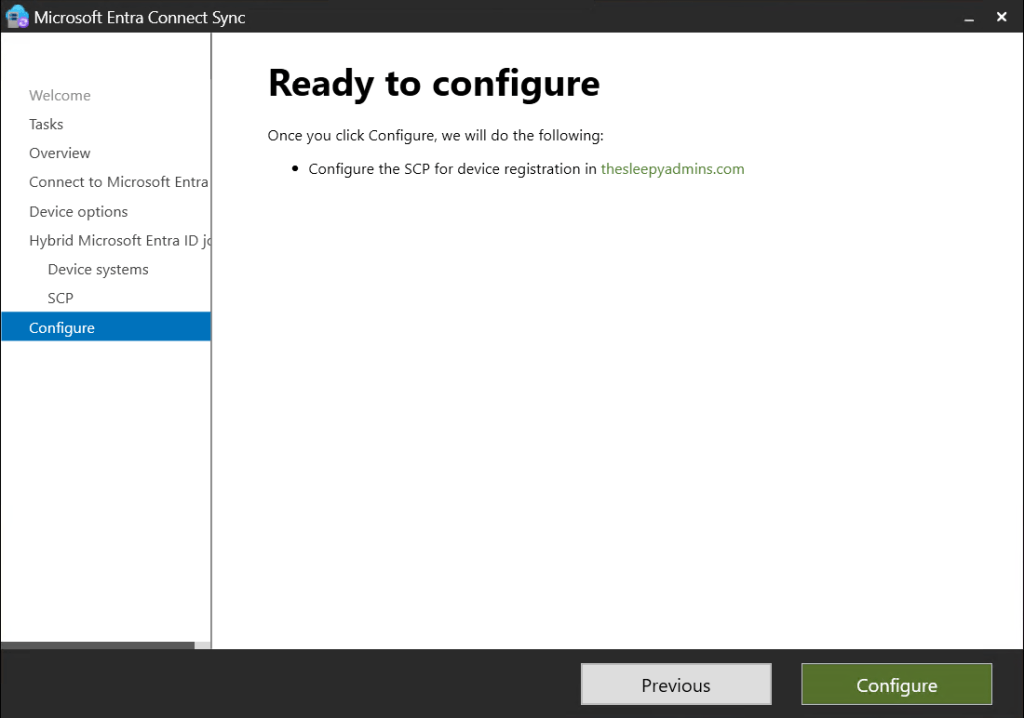
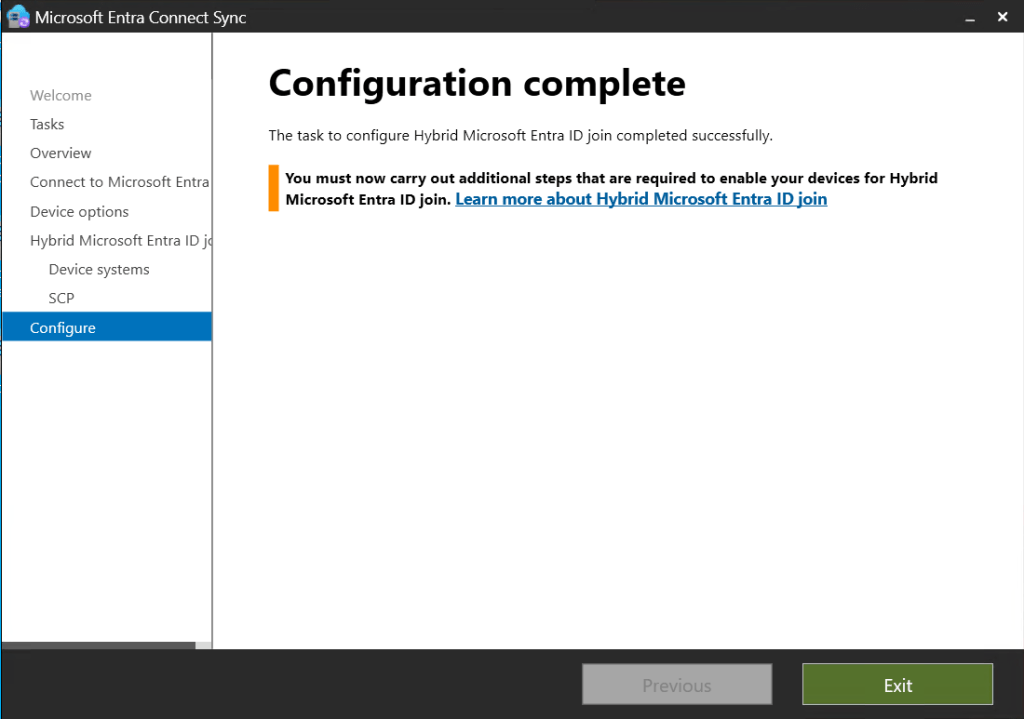
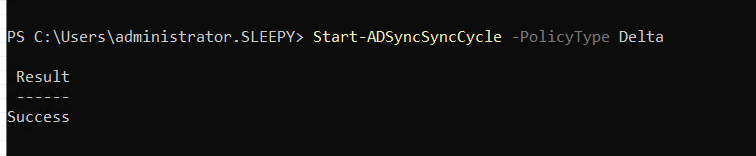
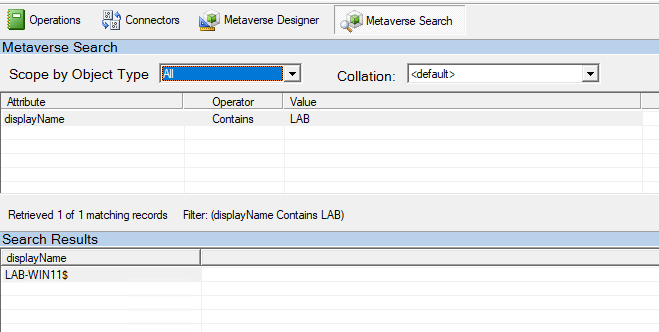
In this post we will be going through the process of enrolling hybrid joined devices to Intune. There are a few different methods to enroll but in this post we will using GPO to enable auto enrollment.
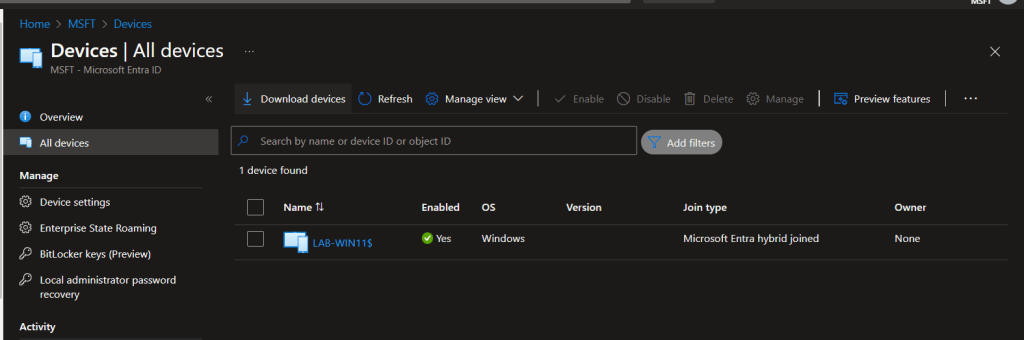
First we need to confirm that MDM is not set on the device. Log on to Microsoft Entra ID portal and go to all devices.
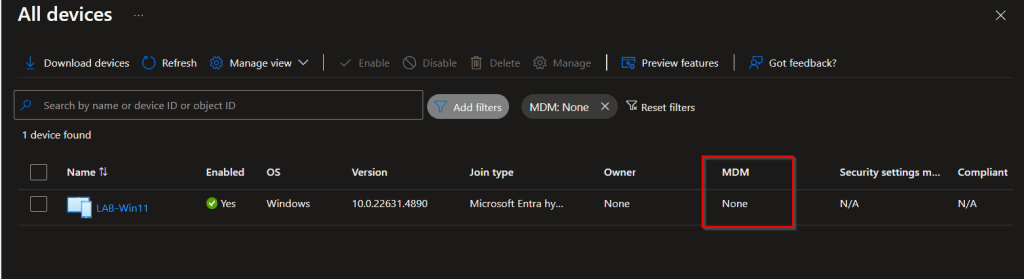
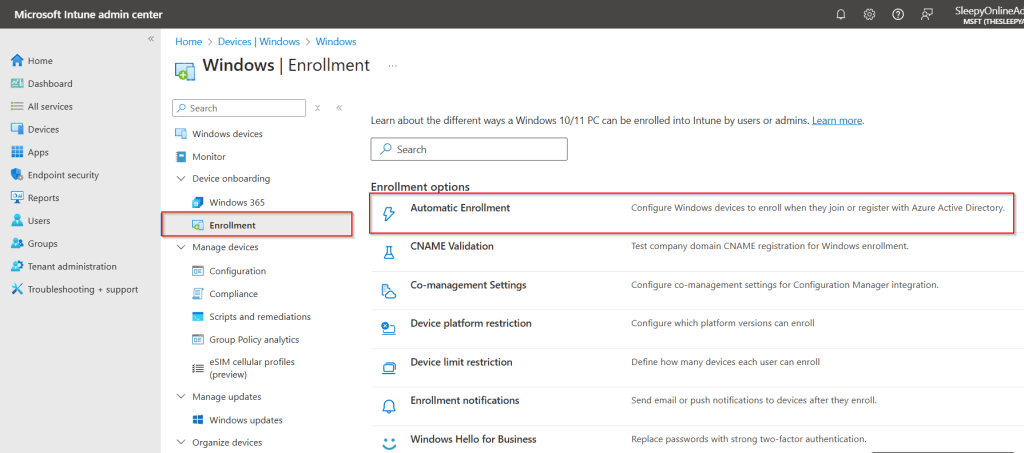
Next we need to check that auto enrollment is enabled, go to Intune > Devices > Windows > Automatic Enrollment.
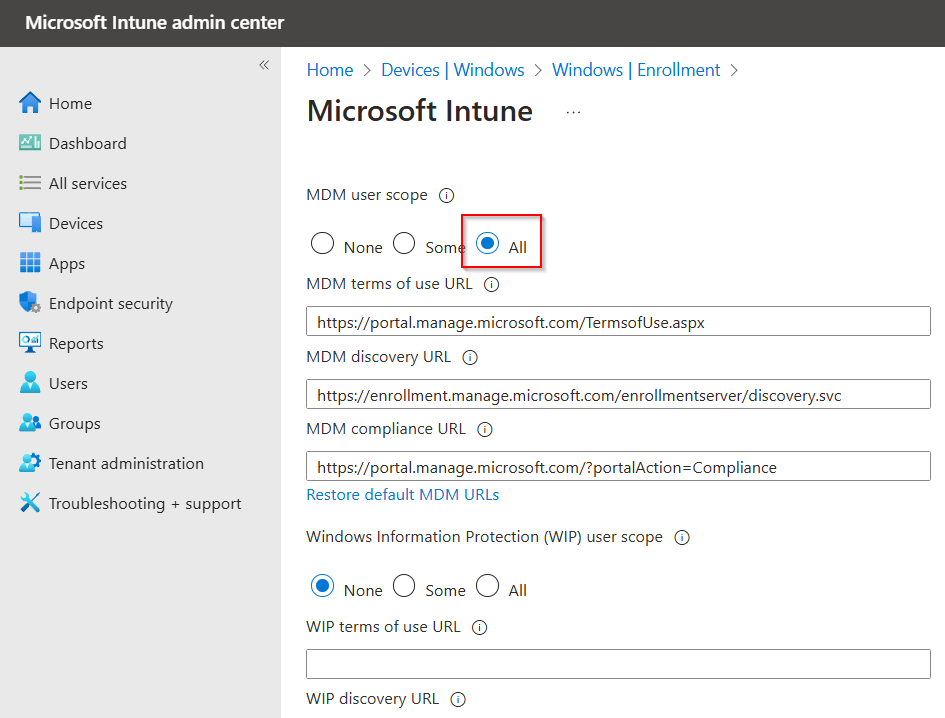
We can either scope MDM to some users or all (we will enabled for all).
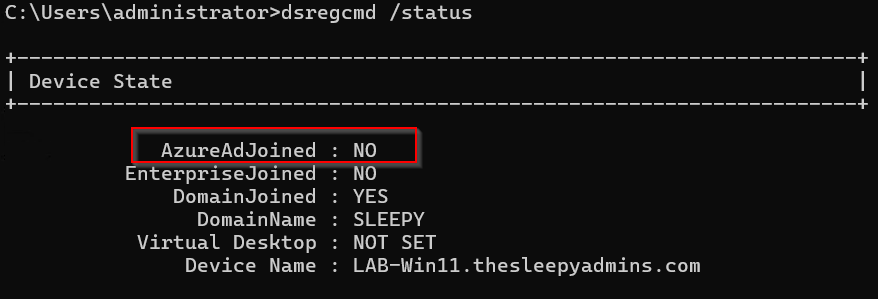
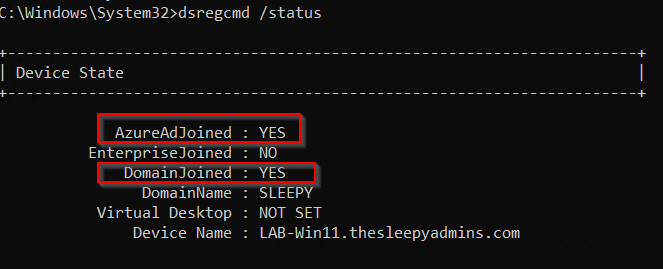
Next we need to confirm the devices that we are trying to enroll is hybrid joined, we can use dsregcmd /status to check the device state.
Once we confirm MDM User enrollment is enabled and the device is hybrid joined, we can create the group policy.
Open gpmc.msc on the domain controller or admin workstation.
Right Click Group Policy Object, click New and give it a name.
Right click on newly created GPO and click Edit
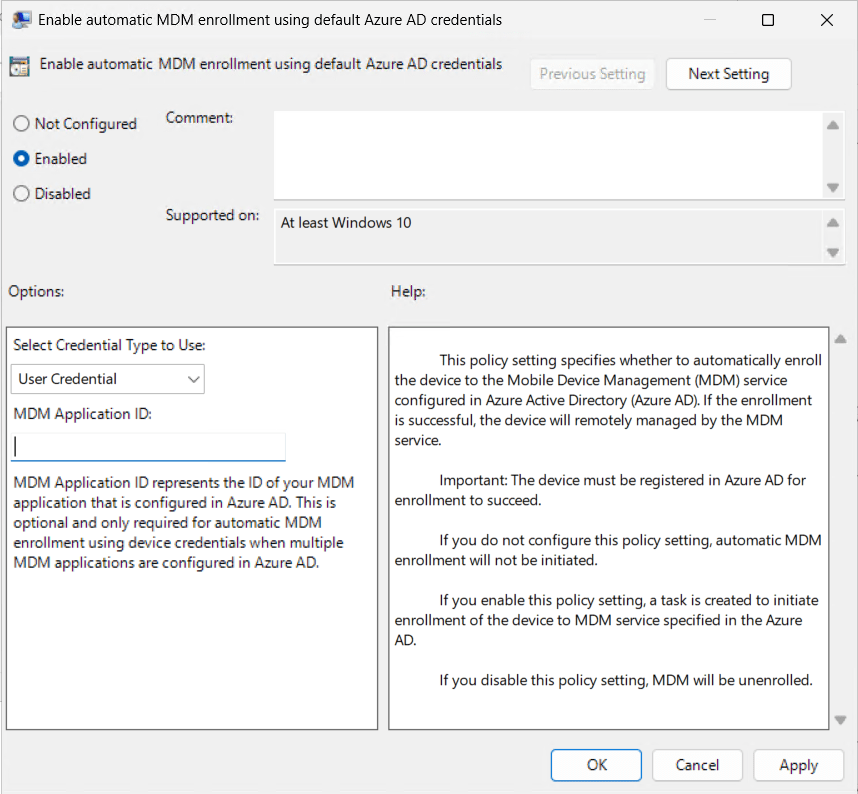
go to Computer Configuration > Policies > Admin Templates > MDM and Double click Enable automatic MDM enrollment
Select Enable, select User Credentials under Select Credential Type.
Next, we need to link the group policy with the OU where the Hybrid joined devices are located.
In group policy, right click on the OU, click link an existing GPO, select Group Policy that we created.
Go to the device and run GPUPDATE /force
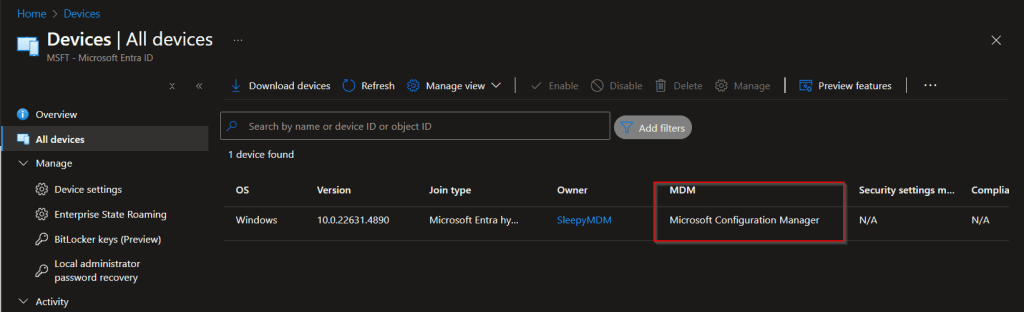
It can take a while for the client to register in the Azure portal. Once it has should see MDM change in my case its to ConfigMgr as I still have the ConfigMgr agent installed.
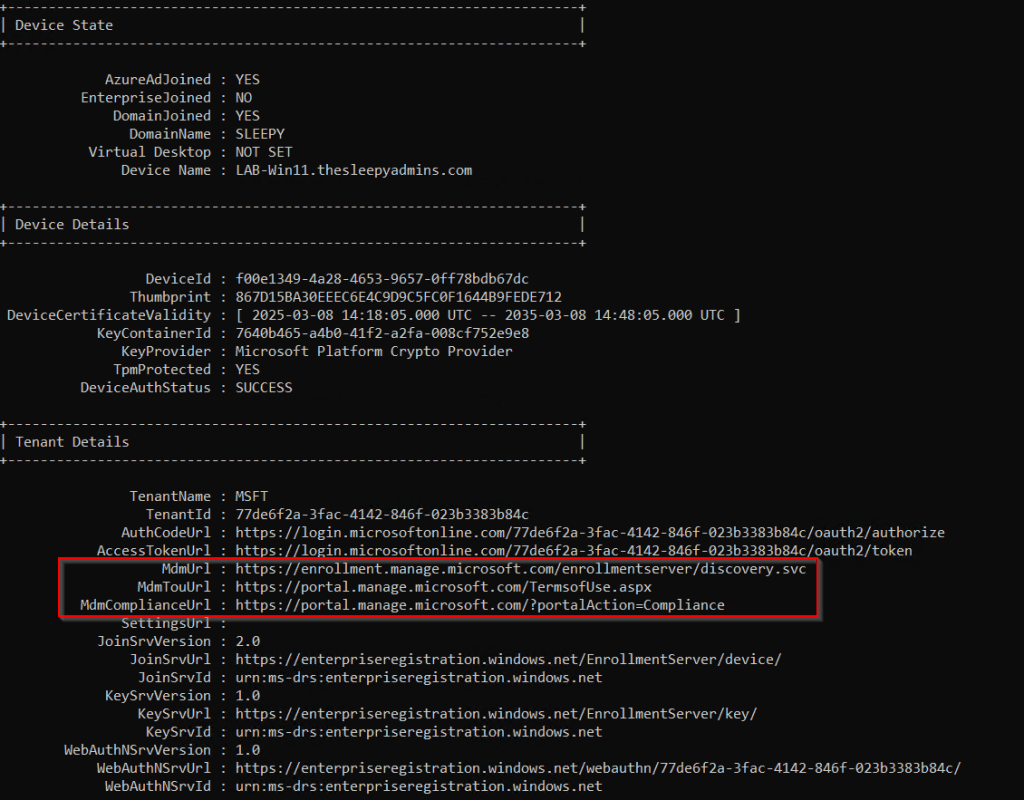
We can run dsregcmd /status to view that the MDM urls have been configured.
We can also check Intune to confirm the device shows.
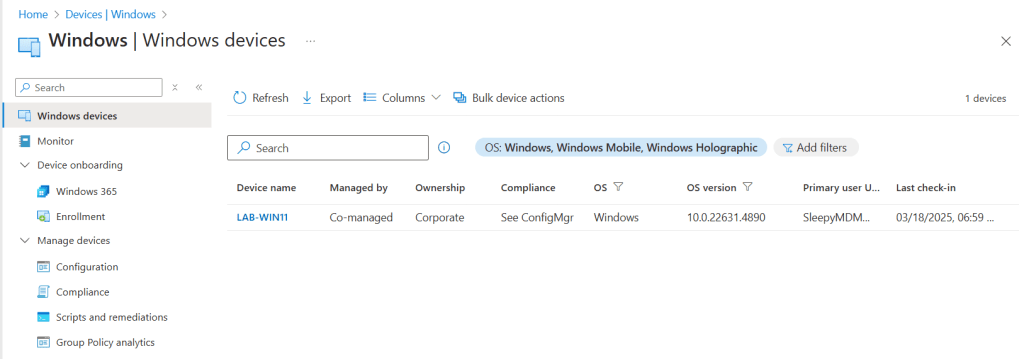
This was a quick overview of setting up auto enrollment for hybrid devices to Intune.