In this post we will be going through using different filter types in Microsoft Graph SDK.
Using filters is useful when trying to return specific results or subset of data.
To check if a command supports filtering we can look up the command on the Microsoft Learn page or try -Filter.

There a few different operators we can use for filtering below is the full list.
- eq
- not ne
- startswith
- endswith
- in
- le
- ge
- not and endswith
- not and startswith
- not and eq
- not and in contains
- has
Once we know the command supports filtering, we need find a property to filter on for users we will use display name.
Get-MgUser -Filter "DisplayName eq 'Name'"

To find all displaynames that start P we can use startsWith(DisplayName, ‘value’)
Get-MgUser -Filter "startsWith(DisplayName, 'P')"

To filter using a variable we can create a new variable with a value and call that in side the filter. This can be use when doing foreach loops to go through each object in an array.

We can also use filtering to return objects by date, the date has to be formatted in a specific way or the filter will error out.
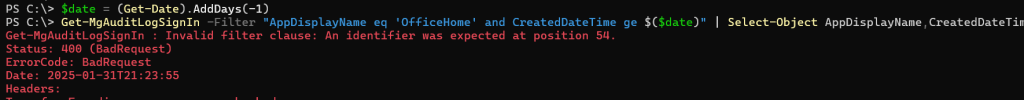
The data has to be yyyy-MM-ddT00:00:00Z To get the correct date format we can use ToString and the format.
$date = (Get-Date).AddDays(-30).ToString('yyyy-MM-ddT00:00:00Z')
Get-MgAuditLogSignIn -Filter "AppDisplayName eq 'OfficeHome' and CreatedDateTime ge $($date)" | Select-Object AppDisplayName,CreatedDateTime

Filtering is an import to learn when using Microsoft Graph without it, it can be difficulty to find the right data or objects.
Filtering also helps improve performance and reduce the amount of data retrieved from Microsoft Graph.